Capabilities
| Resource | Sync | Provision |
|---|---|---|
| Accounts | ||
| Groups | ||
| Roles |
Gather Google Workspace credentials
Configuring the connector requires you to pass in credentials generated in Google Workspace. Gather these credentials before you move on.Create a new project
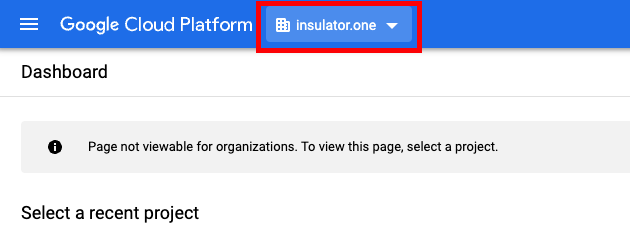
As a Google Workspace Super Admin, sign in to https://console.cloud.google.com.
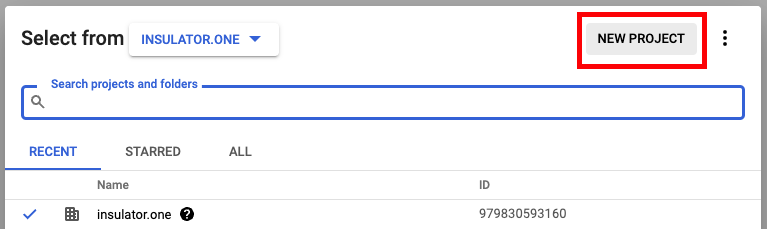
Create a new project for your organization: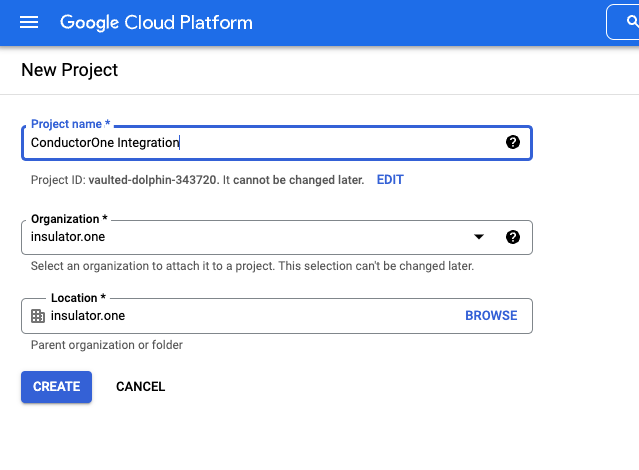
- Project Name: Choose a names, such as “ConductorOne Integration”
- Organization/Location: Choose the appropriate Organization/Location

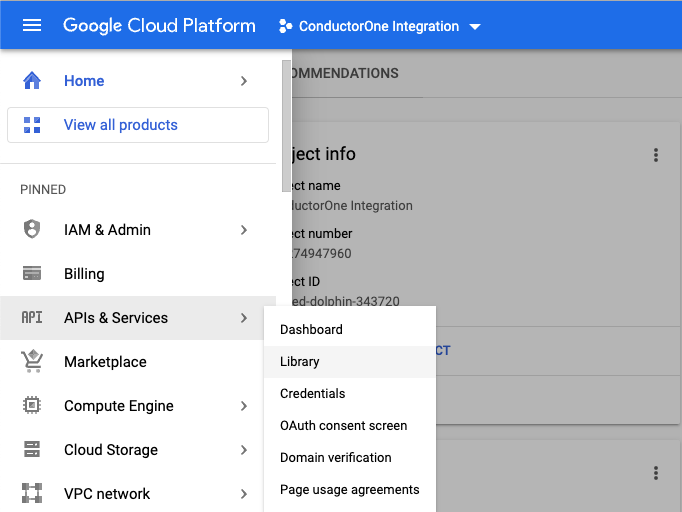
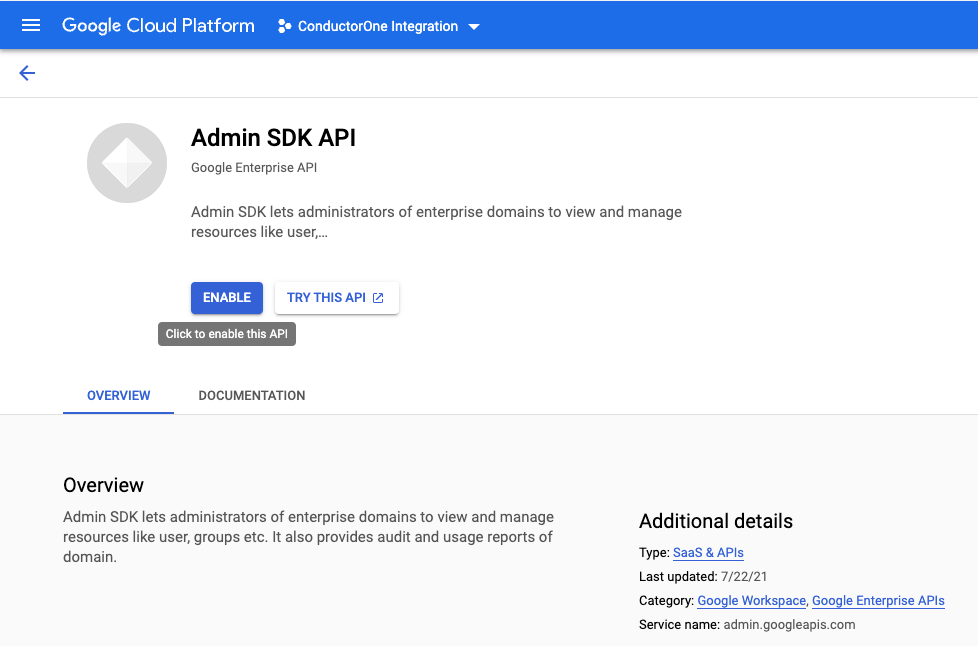
Enable the API
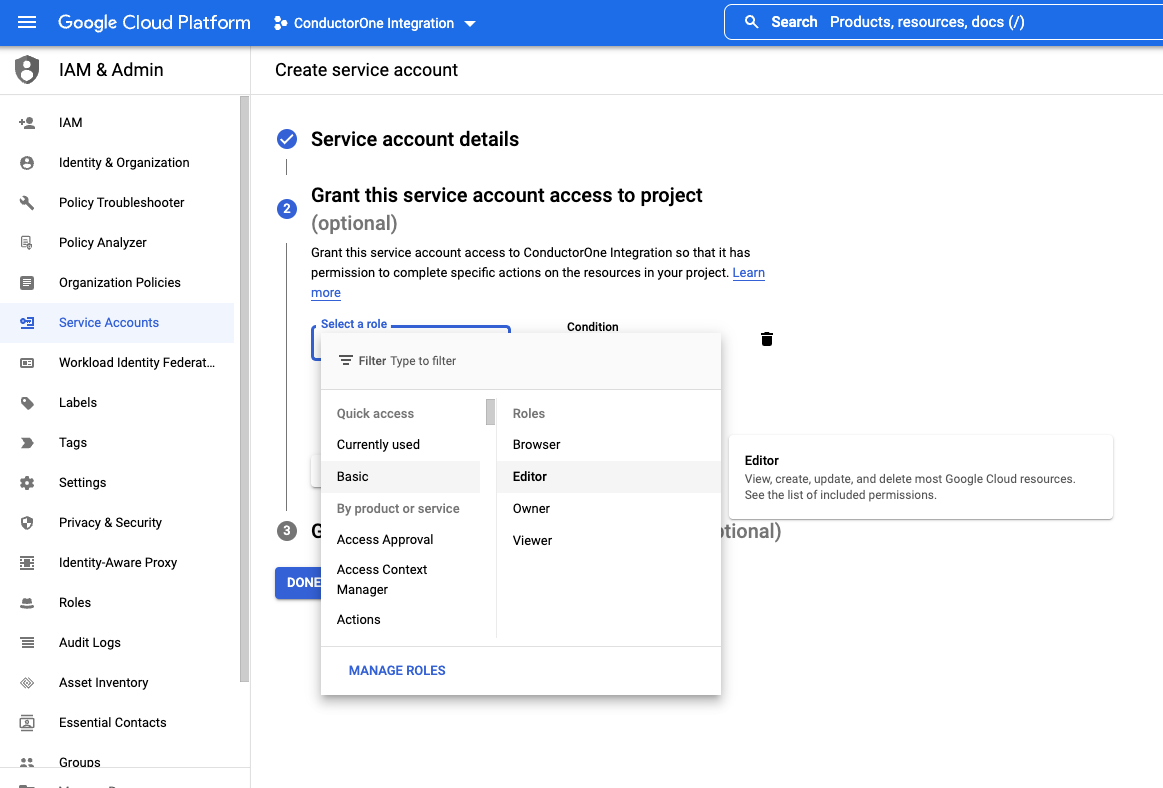
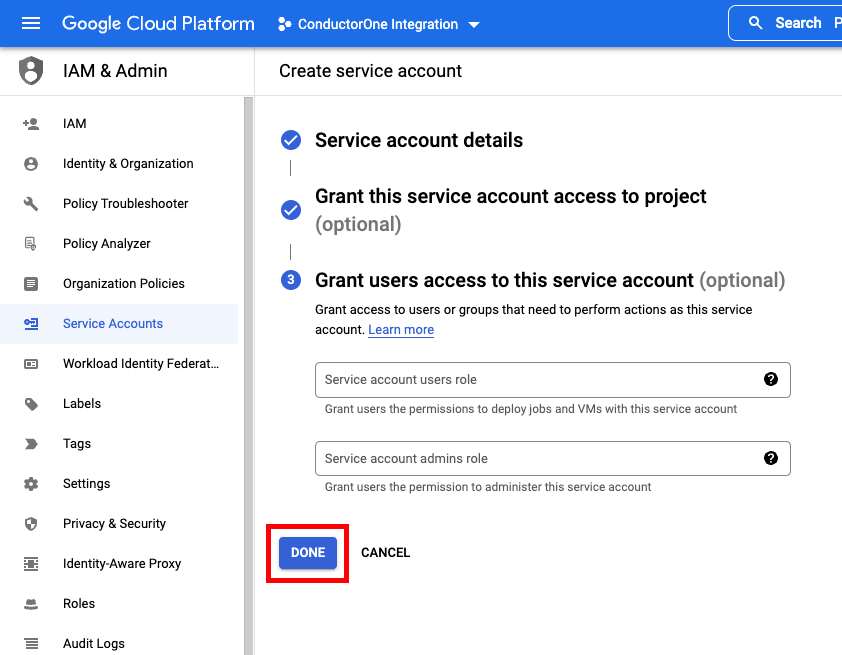
Create a service account
Under Service account details, fill in the following: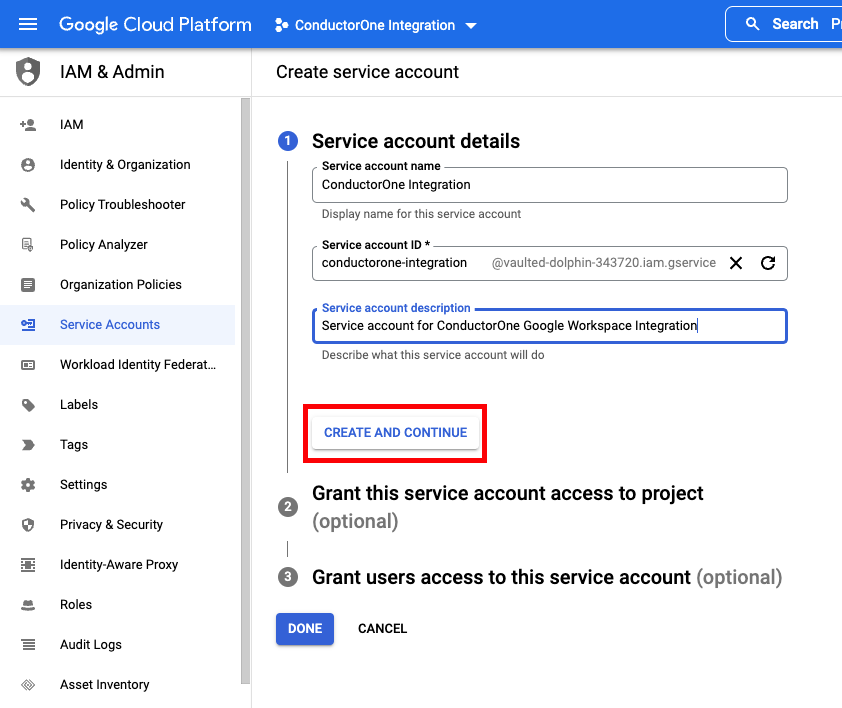
- Service account name: ConductorOne Integration
- Service account description: for example, “Service account for ConductorOne Google Workspace Integration”
- Click CREATE AND CONTINUE

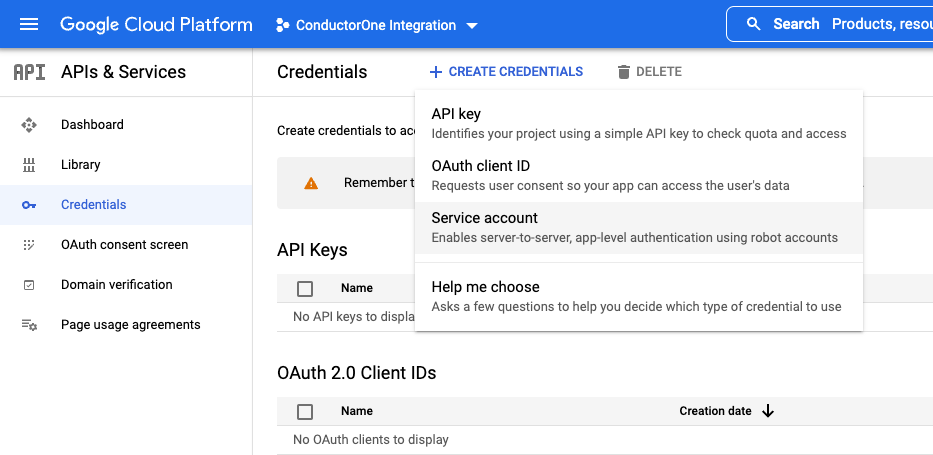
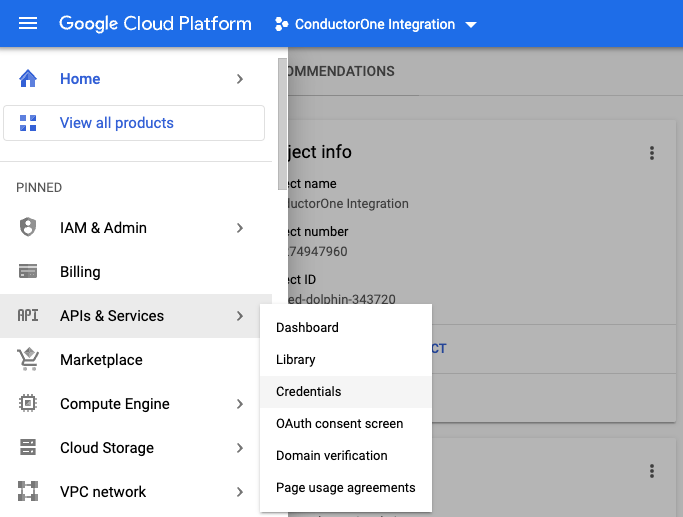
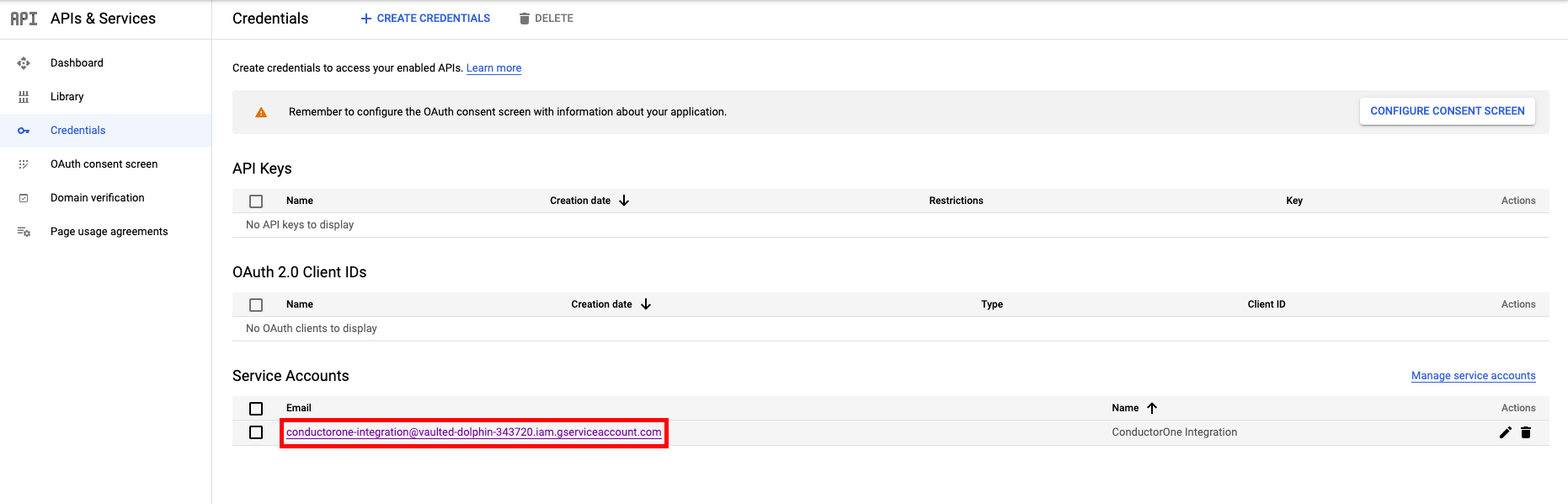
Get credentials
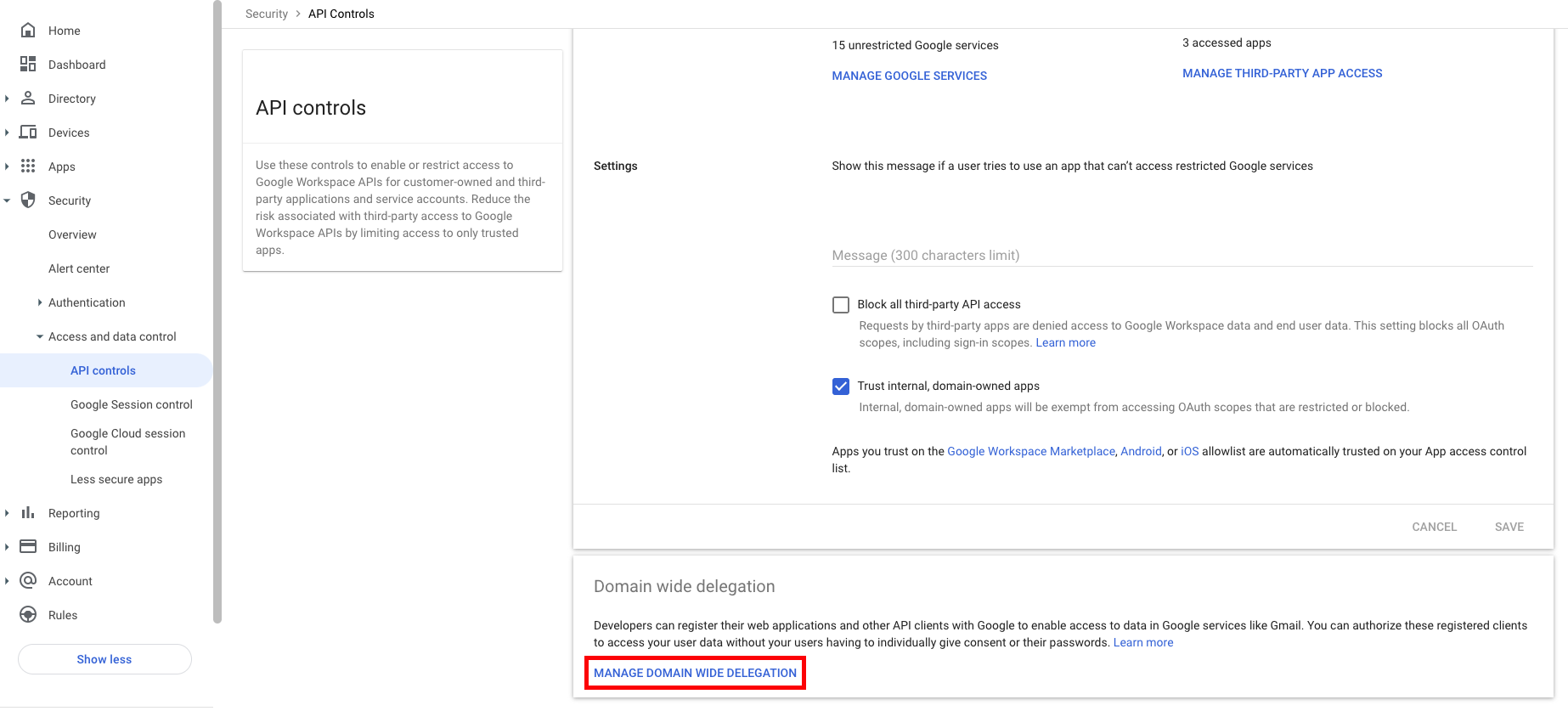
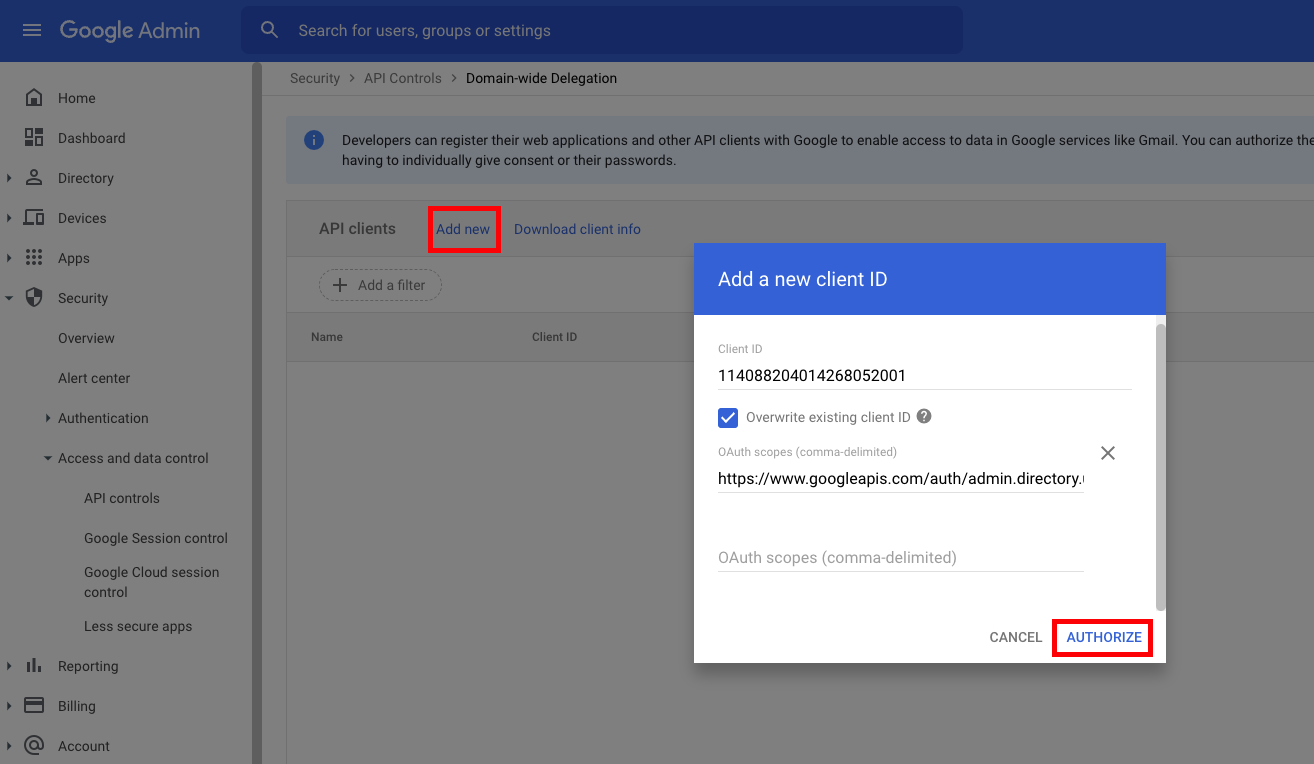
Add the service account to Google Workspace
Go to https://admin.google.com as a SUPER ADMIN.
Click Add new and fill out the form:
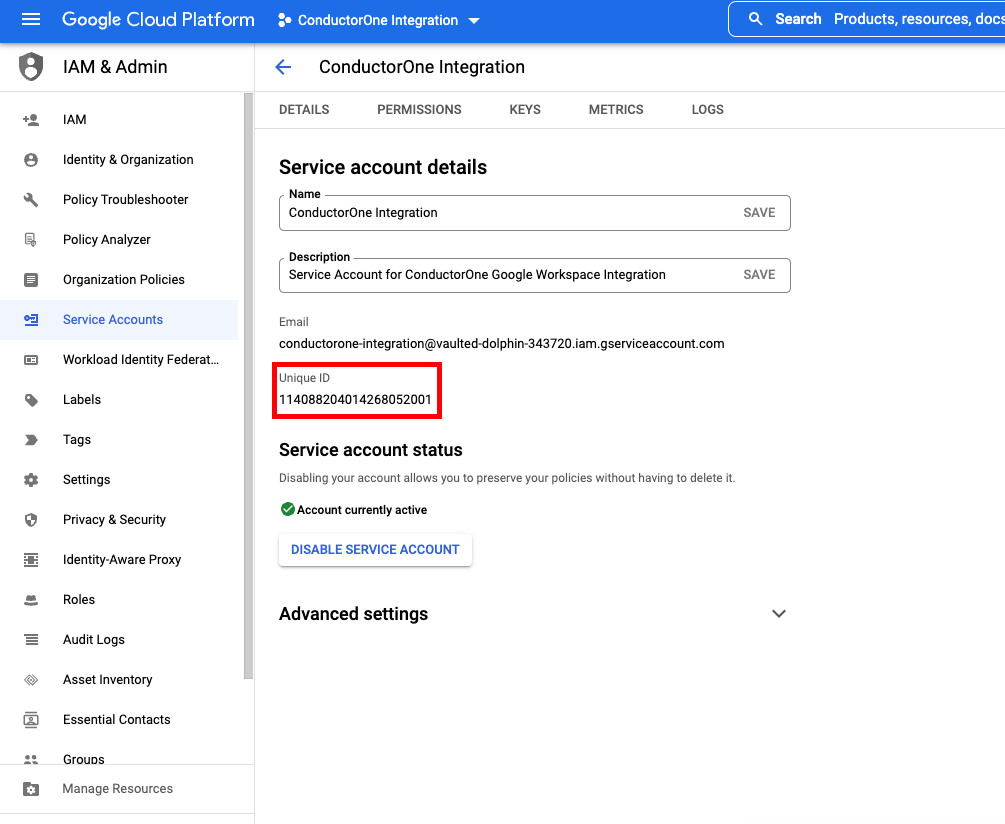
- Client ID: The service account’s unique ID
-
OAuth Scopes: Copy and paste in the relevant scopes
Use the following scopes to give ConductorOne READ access (for syncing access data):
Here’s an explanation of each scope’s purpose:
-
Scope: https://www.googleapis.com/auth/admin.directory.domain.readonly
Purpose: To identify the primary domain of the Google Workspace account. -
Scope: https://www.googleapis.com/auth/admin.directory.group.readonly
Purpose: To read and sync Google Groups. -
Scope: https://www.googleapis.com/auth/admin.directory.group.member.readonly
Purpose: To read and sync the members of each group. -
Scope: https://www.googleapis.com/auth/admin.directory.rolemanagement.readonly
Purpose: To read and sync roles and their assignments. -
Scope: https://www.googleapis.com/auth/admin.directory.user.readonly
Purpose: To read and sync users. -
Scope: https://www.googleapis.com/auth/admin.reports.audit.readonly
Purpose: To sync usage events and admin events (used in conjunction with incremental sync).
Here’s an explanation of each scope’s purpose:-
Scope: https://www.googleapis.com/auth/admin.directory.domain.readonly
Purpose: To identify the primary domain of the Google Workspace account. -
Scope: https://www.googleapis.com/auth/admin.directory.group.readonly
Purpose: To read and sync Google Groups. -
Scope: https://www.googleapis.com/auth/admin.directory.group.member
Purpose: (Write) To manage group memberships (add or remove users from groups). -
Scope: https://www.googleapis.com/auth/admin.directory.rolemanagement
Purpose: (Write) To manage role assignments (grant or revoke roles). -
Scope: https://www.googleapis.com/auth/admin.directory.user
Purpose: (Write) To provision/deprovision accounts. -
Scope: https://www.googleapis.com/auth/admin.reports.audit.readonly
Purpose: To sync usage events and admin events (used in conjunction with continuous sync). -
Scope: https://www.googleapis.com/auth/admin.datatransfer
Purpose: (Write) To transfer user data between Google accounts.
-
Scope: https://www.googleapis.com/auth/admin.directory.domain.readonly
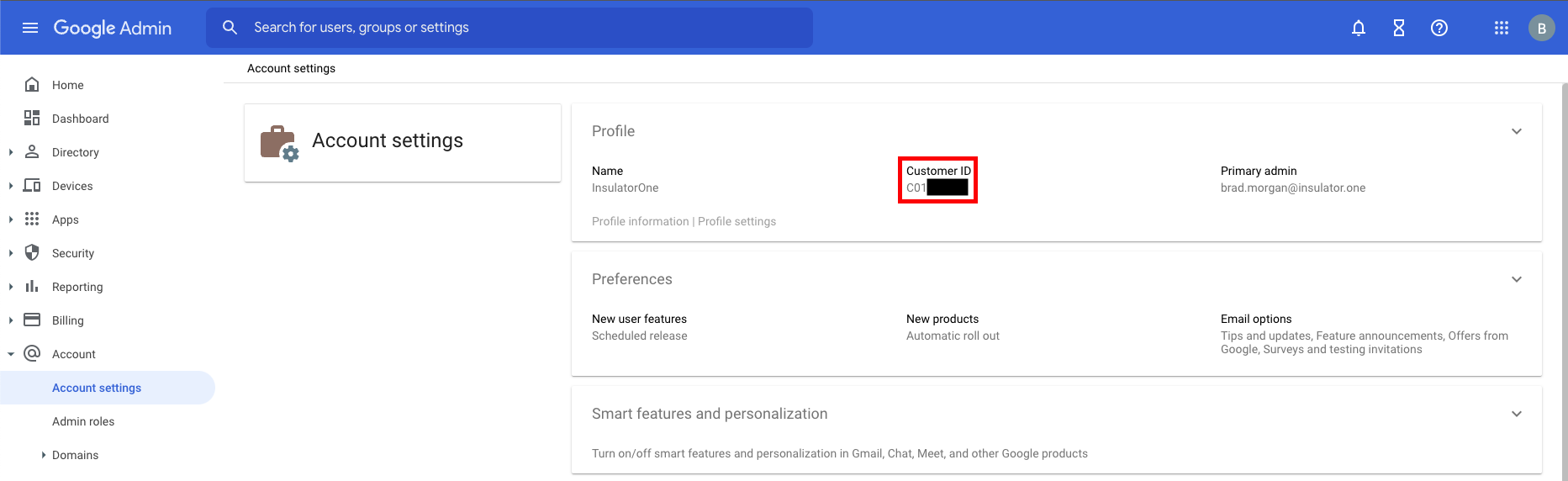
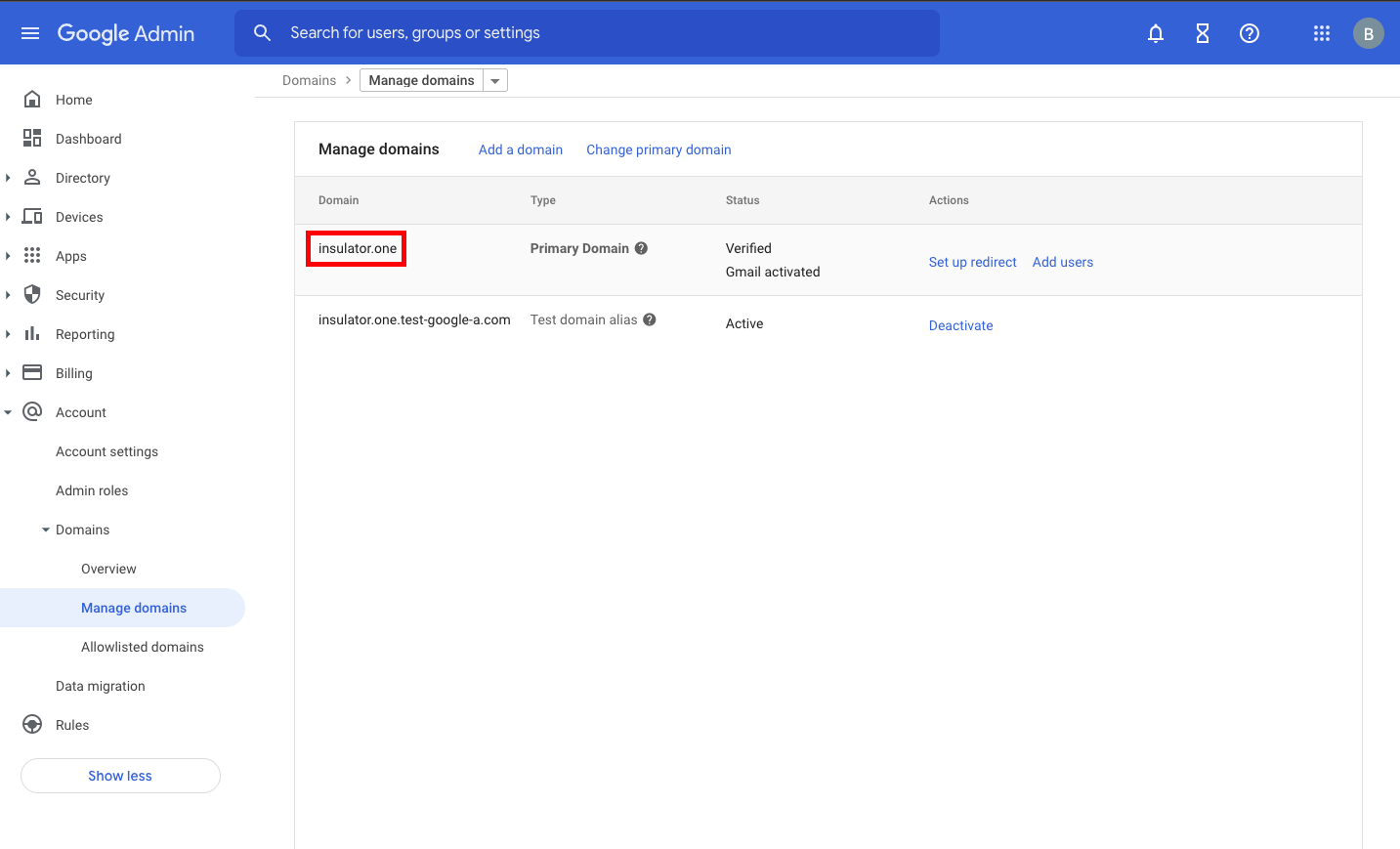
Locate your primary domain
That’s it! Next, move on to the connector configuration instructions.
Configure the Google Workspace connector
- Cloud-hosted
- Self-hosted
Follow these instructions to use a built-in, no-code connector hosted by ConductorOne.That’s it! Your Google Workspace connector is now pulling access data into ConductorOne.
Choose how to set up the new Google Workspace connector:
- Add the connector to a currently unmanaged app (select from the list of apps that were discovered in your identity, SSO, or federation provider that aren’t yet managed with ConductorOne)
- Add the connector to a managed app (select from the list of existing managed apps)
- Create a new managed app
Set the owner for this connector. You can manage the connector yourself, or choose someone else from the list of ConductorOne users. Setting multiple owners is allowed.
Click Next.
- If you are the connector owner, go on to the next step.
- If someone else is the connector owner, you can stop here. ConductorOne will notify the connector owner by email that their help is needed to complete the setup process.
Optional. If you want to limit which domains ConductorOne syncs, in the Domain field, enter the primary domain from Step 6. If you leave this field blank, ConductorOne will sync all available domains.
In the Administrator email field, enter the email address associated with your domain or a super admin.
What’s next?
If Google Workspace is your company’s identity provider (meaning that it is used to SSO into other software), the integration sync will automatically create applications in ConductorOne for all of your SCIMed software. Before you move on, review the Create applications page for important information about how to set up integrations with the SCIMed apps.Troubleshooting the Google Workspace integration
When adding permissions to my Google Workspace API Client permissions I get authorization errors
Example error:error using connector deprovision [attempt #3]: error: delete resource failed: googleapi: Error 403: Request had insufficient authentication scopes. Details: [ { "@type": "type.googleapis.com/google.rpc.ErrorInfo", "domain": "googleapis.com", "metadata": { "method": "ccc.hosted.frontend.directory.v1.DirectoryUsers.Update", "service": "admin.googleapis.com" }, "reason": "ACCESS_TOKEN_SCOPE_INSUFFICIENT" } ] More details: Reason: insufficientPermissions, Message: Insufficient Permission
To resolve this issue:
Remove the Google Workspace API Client, then re-add with the correct permissions.