Bring unauthorized SaaS and AI usage out of the dark
Secure your environment and control app sprawl with shadow IT detection and management.







By 2027, 75% of employees will be accessing tech outside of IT’s view.
*Gartner
Shadow IT is a reality—but it doesn’t have to be a risk. ConductorOne discovers unauthorized apps so you can manage them securely.
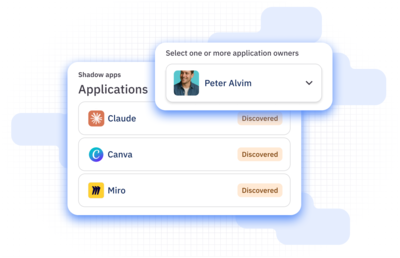
Uncover unknowns
Detect, catalog, and track shadow app usage.
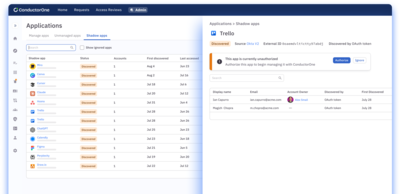
Apply controls
Approve and govern shadow apps like any other app.
Reduce risk and costs
Identify and remediate risky or redundant app usage.

“The overall visibility is a huge win. I don’t have to log into ten different places to figure out who has access to what—I can just go to ConductorOne.”
Paul Yoo, Head of Security Platform

How it works
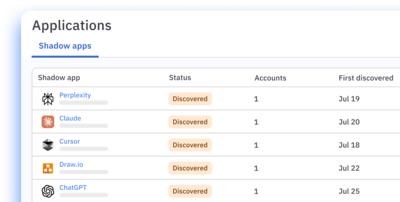
Login detection and tracking
Monitor shadow app signups and logins to determine whether to bring an app under governance.
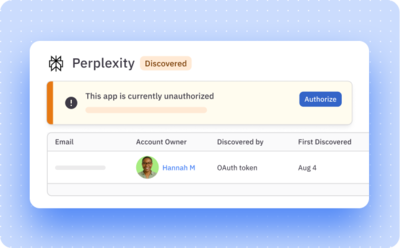
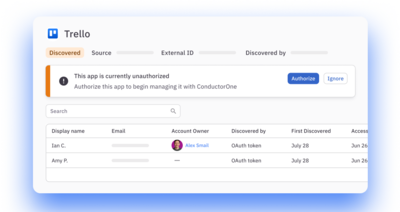
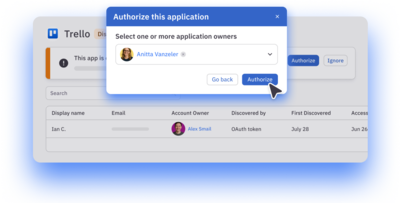
Option to authorize or ignore
Authorize a shadow app to bring it under full control. Choose to ignore low-concern apps—ConductorOne will continue to track logins.
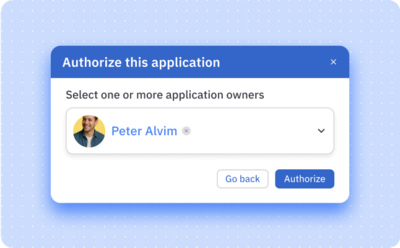
Full-suite governance
Sanctioned shadow apps are like any other app in ConductorOne—enforce access controls, enable self-service, run access reviews, and more.

One platform to power all your identity use cases
Dynamic Access Control
Move to contextual, policy-driven access provisioning
Intelligent Access Reviews
Maintain compliance and improve security without the manual effort
Identity Automations
Build custom identity workflow automations
AI-Native Identity Governance
Manage identity at scale with autonomous AI agents


Security, IT, and GRC teams saving time and improving security with ConductorOne.
Latest on the platform
Guide
The Access Controls Maturity Model
Modernize your identity access controls using ConductorOne’s three-step maturity model.



