Discover and secure non-human identities
No more unknowns—view and manage all your identities in one platform.







Master non-human identities with modern IGA
Get full visibility into AI agents, service accounts, API keys, secrets, and more across your environment.
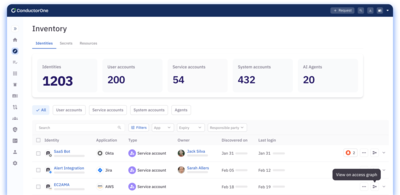
Manage NHI ownership.
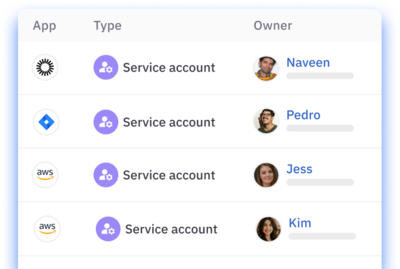
Audit NHI access paths.
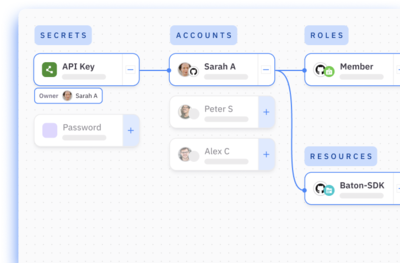
Get alerted to NHI risks.

“We’ve appreciably improved our security posture without spending a bunch of time and money, which is a huge benefit for our customers.”
Matthew Sullivan, Infrastructure Security Team Leader

How it works
Build your NHI inventory
Lightweight connectors ingest, categorize, and inventory service accounts, keys, tokens, and other NHIs from cloud and on-prem apps.
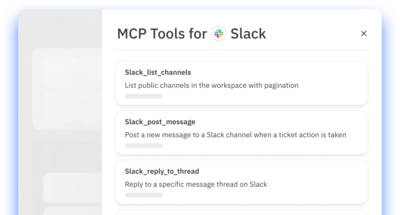
Apply governance
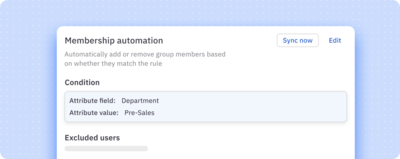
ConductorOne maps NHI relationships and provides flexible controls for managing the NHI lifecycle.
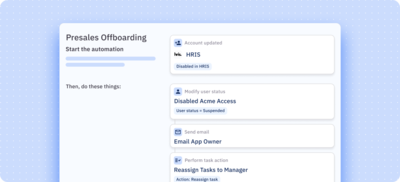
Identify and remediate risks
Real-time alerting allows you to actively remediate risks like unused API tokens and vulnerable service accounts.
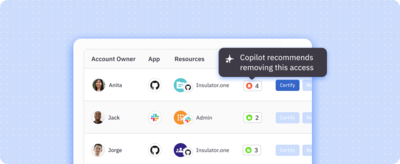
Intuitive, integrated UI
Empower IT, security, and GRC admins as well as end users with a seamless user experience across web app, Slack, and CLI.
One platform to power all your identity use cases
Dynamic Access Controls
Move to contextual, policy-driven access provisioning
Intelligent Access Reviews
Maintain compliance and improve security without the manual effort
Identity Automations
Build custom identity workflow automations
AI-Native Identity Governance
Manage identity at scale with autonomous AI agents


Security, IT, and GRC teams saving time and improving security with ConductorOne.
Latest on the platform

Report
What does agentic AI mean for your identity strategy?
Security leaders are already adapting their identity programs. Read the full report to learn more.

Blog
The Inevitable AI Wave: Modeling the AI Agent Explosion
AI agents are set to outnumber humans 25 to 1. What does that mean for identity and access management? Learn how companies must rethink their approach now or risk being overwhelmed by an imminent surge of short-lived, high-density AI identities.

Podcast
Adding Brakes to Go Faster: Navigating Agentic AI
In this episode of All Aboard, ConductorOne Co-founder Alex Bovee talks with Field CISO Kevin Paige about the evolving world of agentic AI. They dig into why speed without control is dangerous, how trust and security must evolve together, and why human oversight is still essential.

