The entire identity lifecycle — managed.
Streamline and secure the identity lifecycle with powerful workflows and smart, dynamic access controls.
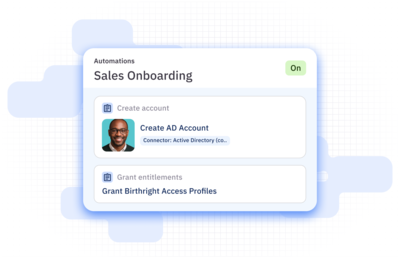







Automate onboarding and offboarding and everything in between.
Provision new users in minutes, rightsize access as roles and attributes change, and ensure leavers are fully offboarded.
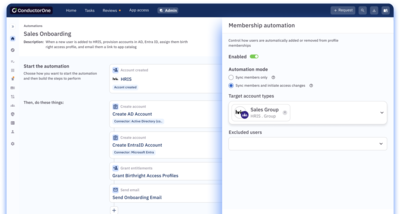
Maximize productivity from day one.
Help workers hit the ground running with easy-to-customize onboarding workflows.
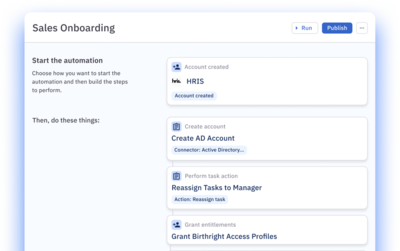
Avoid access creep.
Dynamically adjust access as users’ roles and attributes change.
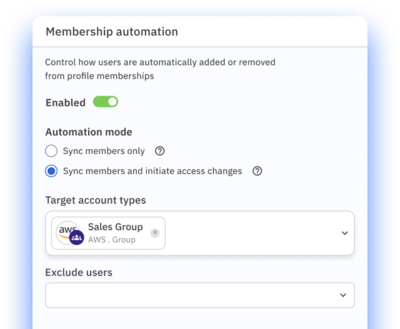
Eliminate orphaned accounts.
Configure custom offboarding workflows that ensure swift, complete deprovisioning.
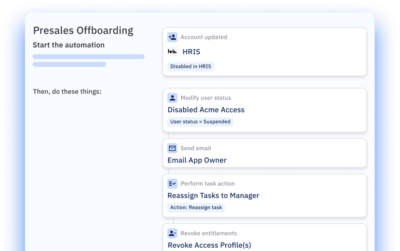
Move to zero standing privileges.
Reduce risk by enforcing just-in-time (JIT) access to any resource. Auto-approve on-call and emergency JIT access.
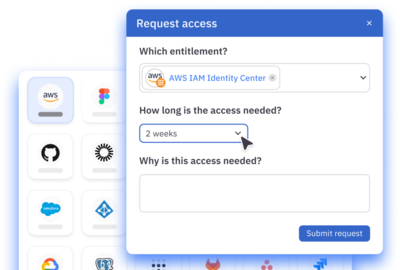

“With the power of ConductorOne’s conditional policies, we can auto-approve. People get the access they need right away.”
Dominic Zanardi, Senior Software Security Engineer II

How it works
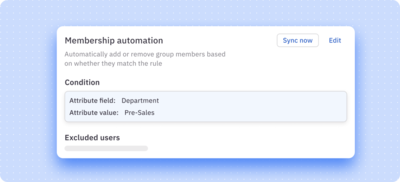
Dynamic access control
Dynamically enroll and unenroll users in access profiles based on contextual attributes like job, role, or location.
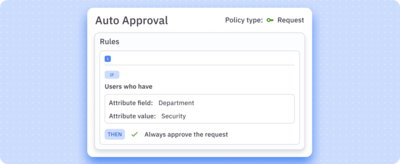
Powerful policies and workflow automation
Create multistep policies that ensure secure approvals and revocations. Build no-code workflow automations suited to your security and business needs.
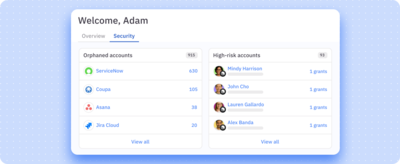
Proactive risk detection and remediation
Identify and eliminate orphaned, overprivileged, or unused access. Launch targeted access reviews anytime based on roles, attributes, account types, and more.
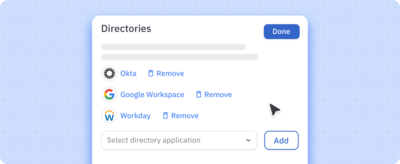
Connectors for every app
Pull fine-grained human and non-human identity data from all your cloud and on-prem apps, infrastructure, directories, homegrown systems, and more into one platform.
One platform to power all your identity use cases
Dynamic Access Control
Move to contextual, policy-driven access provisioning
Intelligent Access Reviews
Maintain compliance and improve security without the manual effort
Identity Automations
Build custom identity workflow automations
AI-Native Identity Governance
Manage identity at scale with autonomous AI agents


Security, IT, and GRC teams saving time and improving security with ConductorOne.
Latest on the platform
Guide
The Access Controls Maturity Model
Modernize your identity access controls using ConductorOne’s three-step maturity model.