Secure hybrid IT systems with unified access controls
Centralize and streamline access controls to protect your most important assets including Active Directory, LDAP, and on-prem apps.
Trusted by IT and Security @







0%
of companies want long, drawn-out IGA implementations.
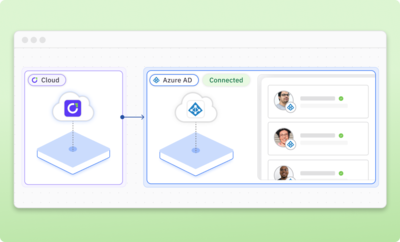
Leverage Active Directory for access control
Connect to your Active Directory instance in minutes to gain visibility into identities, enforce access controls, and automate access reviews.

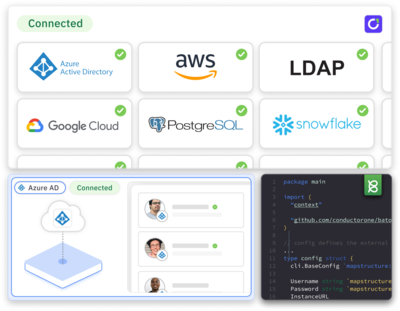
Unify access management across cloud and on-prem systems
Use out-of-the-box connectors to pull fine-grained access data from cloud and on-prem apps, directories, and infrastructure into one control plane — including MySQL, MS SQL, Postgres, MongoDb, LDAP, GitHub, and more.
Learn more about integrations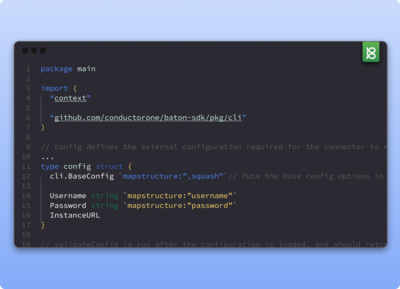
Build custom connectors for homegrown and private apps
Control and monitor access for legacy and sensitive internal systems. Quickly deploy or build connectors for your back office, homegrown, or private on-prem apps—whether API-first or powered by database only—using our open source Baton SDK.
Learn more about Baton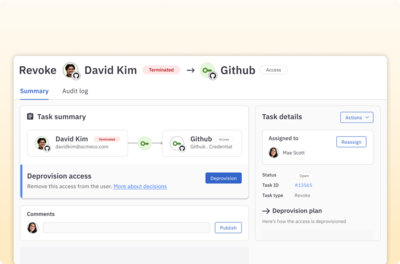
Fully automate on-prem provisioning and deprovisioning
Enable access control decisions made in the cloud to trigger automated on-prem provisioning and deprovisioning.
Learn more about access controls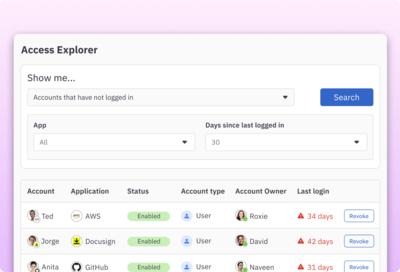
Roll out identity governance for your entire environment
Orchestrate identity governance for all your systems, not just those in the cloud. Enable self-service access, streamline onboarding and offboarding, and enforce policy-driven access controls.
Learn more about next-gen IGA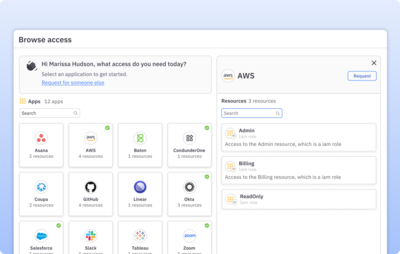
Include on-prem apps in your enterprise app directory
Aggregate all your apps and infrastructure, including on-prem, into a single directory that helps users find and request the apps, roles, and permissions they need.
Learn more about app directory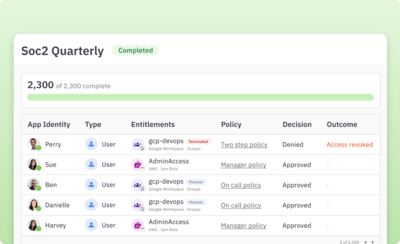
Run access reviews on all systems
Customize and run automated user access reviews with multi-step reviewer policies, Slack notifications, auto approvals, and zero-touch deprovisioning. Generate accurate, auditor-ready reports in one click.
Learn more about access reviews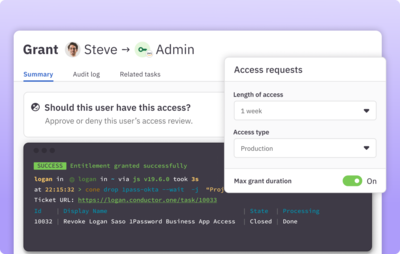
Enable JIT access for on-prem tools and infrastructure
Enforce JIT access to the sensitive infrastructure you manage. Provision needed access on-demand and automatically remove it when no longer needed.
Learn more about JIT access“Being able to review privileged access such as domain admins, enterprise admins, and schema admins within our on-premises Active Directory was a key requirement. ConductorOne was not only the best option but showed a willingness and flexibility to engage in a more strategic partnership long-term.”

Chris Hatfield
Manager of Security and Infrastructure
Features
Out-of-the-box and custom on-prem integrations
Integrate on-prem directories, apps, and infrastructure for complete access visibility. Build custom connectors for on-prem apps and tools not visible from the cloud.
Policy-based access controls
Auto-approve low-risk access and build approval workflows that support conditional and multi-party policies for sensitive permissions.
Just-in-time access
Automate JIT provisioning and deprovisioning to reduce standing privileges to sensitive cloud and on-prem permissions.
Automated access reviews and one-click reporting
Customize and fully automate access reviews and run auditor-ready reports that keep you in compliance.
Unified identity graph
Identify unused, orphaned, and overprivileged accounts and visualize access paths for sensitive roles, resources, and permissions.
Developer-friendly tooling
Get a great builder experience with ConductorOne’s open source Baton SDKs, Terraform support, CLI, and API.

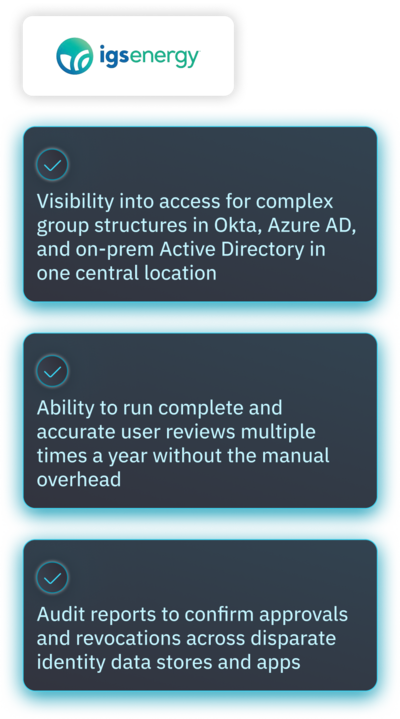
Automating Access Management & Reducing risk for IGS Energy’s Hybrid Environment