Secure your cloud infrastructure with CIEM
View, manage, and protect entitlements across your cloud platforms and data warehouses from one control plane.
Trusted by IT and Security @








Integrate all cloud entitlements into one view
Get comprehensive visibility into access and permissions across your cloud environments with agentless connectors for GCP, Azure, AWS, Snowflake, Databricks, and more.
Learn more about integrations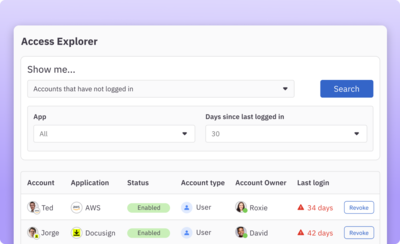
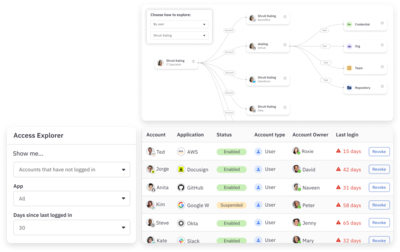
Uncover and remediate risky entitlements
Quickly surface and remove hidden cloud security risks such as orphaned accounts, over-provisioned access, and unused access using fine-grained access queries and built-in remediation.
Learn more about access query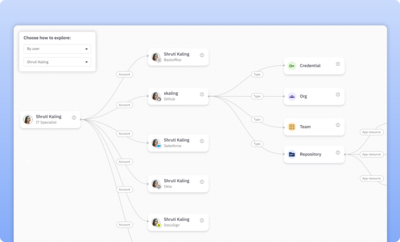
Visualize resource access paths
Visually trace downstream access and permissions to sensitive cloud infrastructure resources and data using an interactive access graph.
Learn more about access graph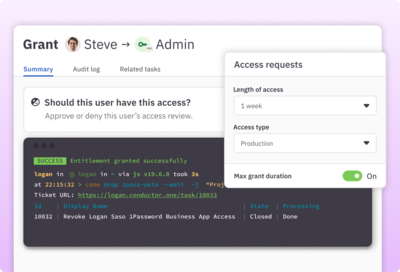
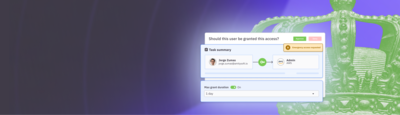
Enforce zero standing privilege with just-in-time provisioning
Move sensitive roles and permissions in your cloud platform and data warehouse environments to JIT access so they can be requested on demand and automatically removed when no longer needed.
Learn more about JIT access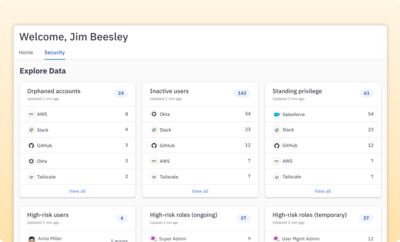
Proactively monitor security risks
Stay on top of your cloud infrastructure attack surface area with a dashboard view of real-time entitlement risks and monitoring of access and permission changes.
Learn more about the security dashboard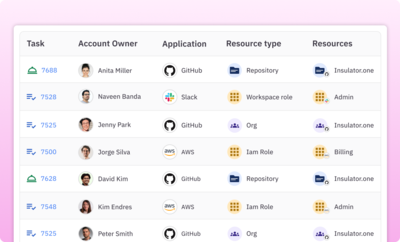
Streamline cloud infrastructure compliance
Run fully automated cloud entitlement access reviews to further mitigate risk and stay in compliance.
Learn more about access reviews“We’re able to minimize the number of users with access to critical systems at a given time. That’s a big security win for us across the board.”

Paul Yoo
Head of Security Assurance

Features
Cloud infrastructure connectors
Agentless connectors the most popular cloud infrastructure services including AWS, GCP, and Azure.
Cloud data warehouse integration
Protect your most sensitive data hosted in Databricks, Snowflake, MongoDB, and other popular cloud data warehouses.
Just-in-time access
Automate JIT provisioning and deprovisioning with flexible policies for temporary, on-call, and break-glass access.
Risk dashboard and monitoring
Monitor cloud access risks by identifying inactive users, standing privilege, and high-risk access in real time.
Access query and graph
Search for unused, orphaned, and overprivileged accounts and visualize access paths for sensitive roles, resources, and permissions.
Fine-grained permission reviews
Run automated entitlement reviews on cloud infrastructure to reduce risk and maintain compliance.