2024 Identity Security Outlook Report
Complex environments, non-human identities, zero standing privileges—learn security leaders’ identity security concerns and priorities for 2024.
Key Insights
We surveyed over 500 IT and security professionals across the US to get a snapshot of the current identity security and access management landscape. The results clearly show that increasing technological and organizational complexity are creating a new wave of identity risks for companies.
Read the report to learn where companies are struggling, where they’re succeeding, and what security leaders are prioritizing for 2024 and beyond.
77%
reported identity-based security incidents.
The majority of security leaders reported instances of cyberattacks or data breaches at their organization in the past year due to improper or overprivileged access.
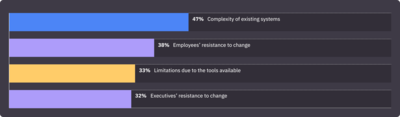
System complexity is today’s top identity security challenge.
81%
of respondents are concerned about the access risks posed by non-human identities.
76%
are managing identities across hybrid environments.
93%
believe enforcing zero standing privileges (ZSP) reduces access risks.

Read the report to learn what security leaders are prioritizing for 2024 and beyond.
More resources

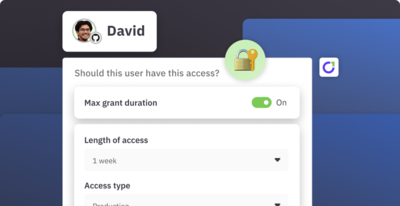
Gain visibility. Streamline access. Automate compliance.
Learn how ConductorOne simplifies identity governance and secures access across even the most complex environments.