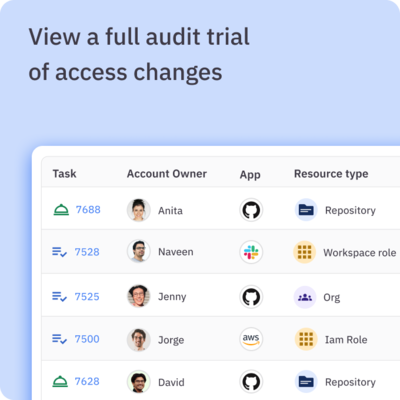
One identity platform — full control and compliance
Take advantage of ConductorOne’s modern IGA platform to:
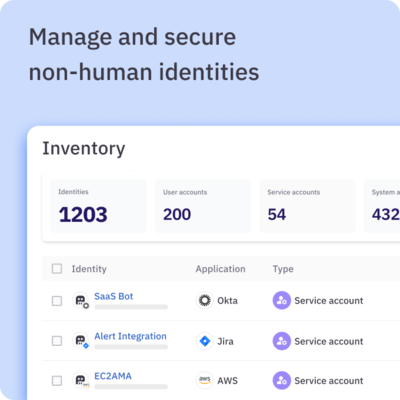
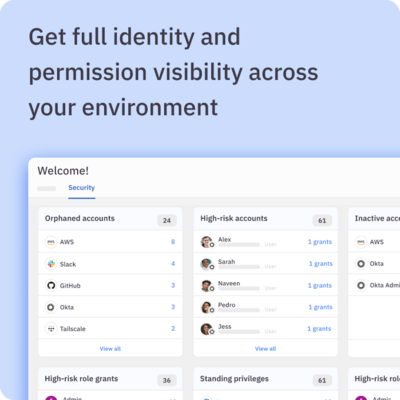
- ✅ Get full visibility across your environment — human and non-human identities alike
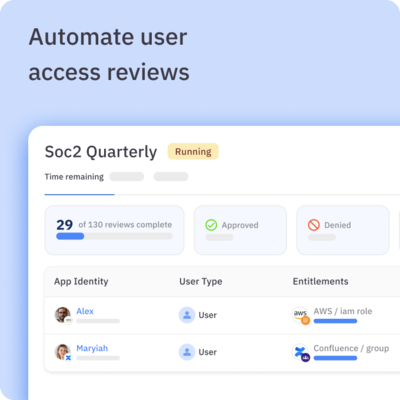
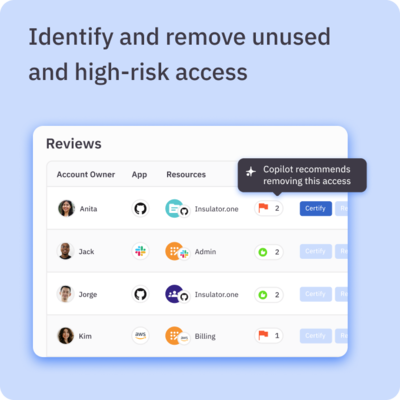
- ✅ Reduce access review efforts by 97%
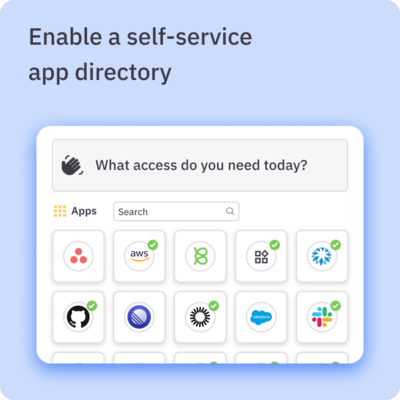
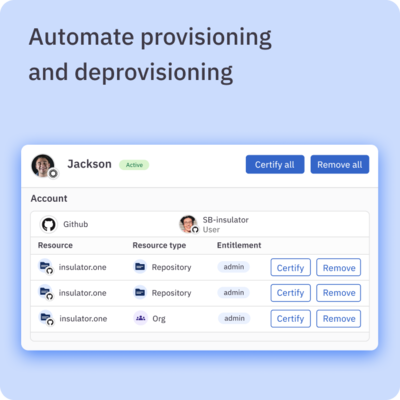
- ✅ Ensure employees can access the apps they need
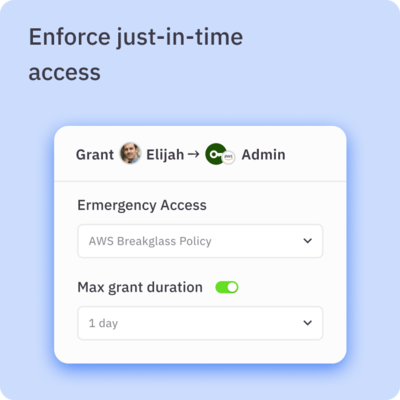
- ✅ Move sensitive permissions to just-in-time access
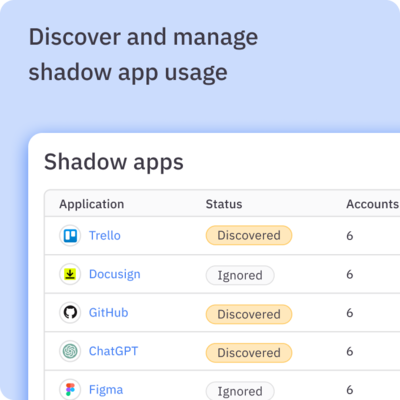
- ✅ Quickly find and remediate risky access and shadow applications
Get ready to 💜 your IGA







With ConductorOne you can
Learn how security, IT, and GRC teams use ConductorOne to be more secure and productive
97%
reduction in time to prepare access reviews
95%
reduction in effort to process access requests
<1
Monthaverage time to go live