Legacy IGA isn’t your only option
Sail away from old-school IGA with a modern solution that fits your tech stack.

Rapid cloud adoption has transformed identity governance needs, and technology has evolved well beyond the 20-year-old legacy tools on the market today.
Old-school IGA is time consuming to deploy and cumbersome to use
- Loooooooooong implementation times and high service costs
- Heavy lift to bring on new apps and systems
- Poor user experience with old-school look and feel in web only
- Standing access is long-lived, little to no risk reduction

Modern IGA is built for your existing identity and tech stack
- Quick time to value, one month average time to go live
- Out-of-the-box integrations, extensible platform, open API
- Modern, intuitive user experience in web, CLI, Slack, or Jira
- Security-first product with intelligent, risk based access controls
Why ConductorOne is different
Fast time to value
System1 integrated with critical applications like AWS and Okta and launched their first access review campaign in just three weeks.

Centralize, view, and activate your identity and access data.
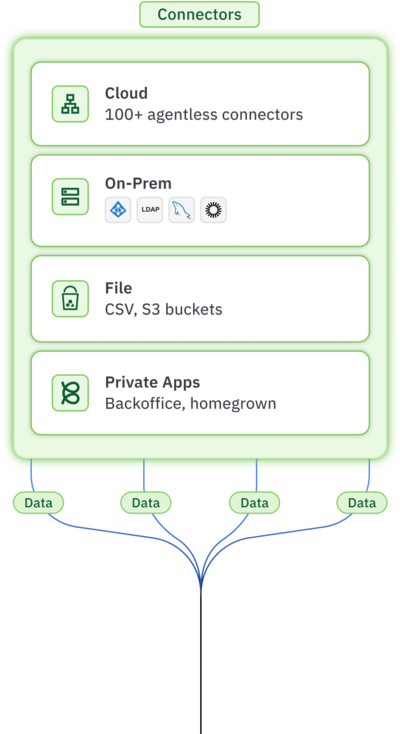
AI-powered risk analysis and helpdesk automation
Unified data layer that provides complete visibility and granular control of access across environments
Shadow IT, effective access, orphaned, high-risk, and over privileged accounts
Usage-based revocation, automated provisioning, time-bound deprovisioning, conditional policies
Automated access reviews, separation of duties, self-service, JIT access, on and offboarding
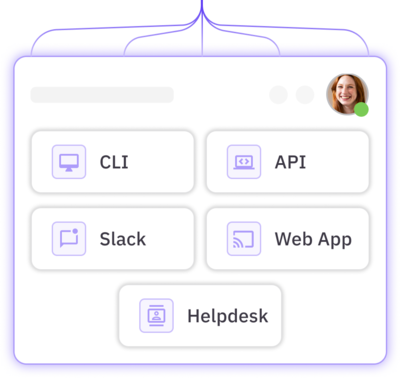
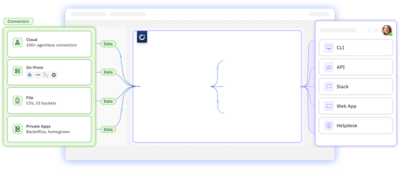
Unified data layer that provides complete visibility and granular control of access across environments
AI-powered risk analysis and helpdesk automation
Shadow IT, effective access, orphaned, high-risk, and over privileged accounts
Usage-based revocation, automated provisioning, time-bound deprovisioning, conditional policies
Automated access reviews, separation of duties, self-service, JIT access, on and offboarding