Provisioning and Deprovisioning Examples, Types, Methods, and Best Practices
Provisioning isn’t a one-time event but part of a lifecycle that includes maintenance and eventual deprovisioning. The lifecycle follows the user’s role changes and employment status within an organization.
What Is Provisioning?
Provisioning refers to the process of setting up and configuring the necessary hardware, software, and access permissions needed for users and systems to function within an organization’s IT environment.
In simpler terms, provisioning involves creating, updating, and managing access to hardware and software.
This process is essential for ensuring that all users have the right tools and access rights from the start, tailored to their specific roles and responsibilities within an organization.
How Provisioning Works
Here’s an example: Imagine a new employee joins your company. The IT department must ensure that this employee has everything needed to start working from day one.
This process includes several steps:
- Hardware Provisioning. Assigning the right type of computer (laptop or desktop), smartphone, and other necessary devices.
- Software Provisioning. Installing and configuring required software applications, such as email clients, office suite programs, project management tools, and any specialized software that the role may require.
- Access Permissions. Setting up user accounts for access to corporate networks, databases, and cloud services. This includes providing credentials for various systems and ensuring the user has the right level of access according to their job role.
- Security Settings. Implementing security protocols such as VPN configurations, antivirus software, and encryption tools to protect the organization’s data and the user’s privacy.
💡 The goal of provisioning is to streamline the process of integrating new users and technology into the organization, ensuring they are productive and secure without delay.
What Is Deprovisioning?
Deprovisioning involves revoking all authorized access privileges and recovering any assets distributed to the user.
This process affects various levels of access, including network credentials, software licenses, email accounts, and specific data permissions. It can also involve physical assets like keys, badges, and equipment.
For the most part, deprovisioning is typically triggered by events such as employee termination, role changes, or the end of a contract with external vendors.
How Deprovisioning Works
Let’s take a cue from the provisioning example above. Consider a scenario where an employee leaves your company.
To maintain security and manage resources effectively, the IT department must undertake several steps to ensure that the employee’s access to company resources is properly revoked.
This process includes:
- Revoking Access. Disabling logins and passwords for all systems the employee had access to, including corporate networks, email accounts, and proprietary software.
- Recovering Assets. Collecting any company-owned hardware, such as laptops, mobile devices, and security badges. This also includes ensuring that all data on these devices is either securely transferred back to the company or properly erased.
- Software License Management. Removing the user from licenses for software tools and applications to free up resources for other users and prevent unauthorized access.
- Security Protocols. Updating security settings that might have been specifically tailored for the departing employee, such as firewall rules, access controls, and encryption keys.
💡 Ensure you document your deprovisioning process to maintain an audit trail for security and compliance purposes. This shows the company has taken appropriate steps to safeguard its resources.
What Are the Types of Provisioning?
There are five main types of provisioning; user provisioning, service provisioning, cloud provisioning, network provisioning, and server provisioning.
User Provisioning
This involves creating and managing user accounts across IT systems and applications. It includes assigning roles, managing permissions, and ensuring that individuals have appropriate access to resources based on their job requirements.
Example of User Provisioning
Suppose a new marketing analyst named Alice joins a company. During her user provisioning:
- An IT administrator creates an account for Alice in the company’s user directory.
- Alice is assigned the role of “Marketing Analyst,” which automatically grants her access to the marketing department’s shared drives, the company’s CRM software, and specific data analytics tools.
- The administrator also configured permissions to allow Alice read and edit marketing campaign files but not access confidential financial reports.
- As Alice undergoes training, additional temporary permissions might be granted to access certain training resources.
If Alice later transitions to a different role in the company, her access rights would be updated to match her new responsibilities, or her account would be deactivated upon her departure from the company.
Service Provisioning
Service provisioning refers to the setup and deployment of software applications and services to users or groups within an organization. It includes the configuration of servers, databases, network services, and cloud-based resources to support various business functions.
Example of Service Provisioning
Consider a company deploying a new customer relationship management (CRM) system:
- The IT department selects a CRM platform that integrates well with the company’s existing sales and marketing tools.
- They configure the server environments and set up databases that will store customer data securely.
- The CRM is integrated with the company’s email system and analytics tools to enhance functionality.
- The system is tested to ensure it can handle the expected number of concurrent users without performance issues.
- Roles are defined within the CRM to limit access based on departmental roles, ensuring that only relevant staff can access sensitive customer information.
Cloud Provisioning
Cloud provisioning includes all activities related to deploying and managing cloud environments. This type of provisioning can be dynamic, allowing for the scaling of resources up or down based on demand, and can include Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS) setups.
Example of Cloud Provisioning
A tech startup decides to launch a new mobile app, requiring backend services hosted in the cloud. The process would involve:
- Selecting a PaaS solution to avoid the complexity of managing hardware and OS-level configurations.
- Allocating resources such as computing power and database services tailored to their initial user base size.
- Configuring the environment with necessary development tools, database systems, and security settings.
- Integrating with third-party services like payment gateways and email notification services.
- Implementing security measures including authentication protocols and data encryption.
- Enabling auto-scaling features to automatically adjust resources as user demand changes.
Network Provisioning
Network provisioning involves the setup and management of network infrastructure to ensure efficient and secure data transmission within an organization and to external internet connections. A few examples include configuring network elements and services like bandwidth, routers, switches, and firewalls.
Example of Network Provisioning
Consider a company expanding its office space and needing to extend its network to new areas:
- The IT team designs a network extension that includes additional switches and wireless access points to cover the new space.
- They select enterprise-grade switches and secure Wi-Fi equipment that supports the latest wireless standards.
- The new devices are configured to integrate seamlessly with the existing network, including setting up VLANs for different departments for security and traffic management.
- Advanced security configurations, such as setting up segmented wireless access for guests, are implemented.
- The entire extended network is tested to ensure connectivity, proper data routing, and robust security.
Server Provisioning
Server provisioning involves setting up and preparing server hardware and software for its intended tasks within a network. This type of provisioning ensures that servers are configured, maintained, and optimized to handle their designated workloads, whether they host applications, manage databases, or perform computational tasks.
Example of Server Provisioning
Imagine a company launching an e-commerce platform. They need to provision a new server to host their website:
- The IT team selects a server with adequate RAM and powerful CPUs to handle web traffic and transaction processing.
- They install Linux because of its reliability and strong community support for web hosting environments.
- Network settings are configured to ensure the server can handle incoming e-commerce traffic effectively.
- Web server software (like Apache or Nginx) and the e-commerce platform software are installed and configured.
- Security measures, including a web application firewall and SSL certificates, are implemented to protect user data and transactions.
- The server is tuned for performance by optimizing the web server and database settings to handle multiple simultaneous connections.
What Are the Methods of Provisioning?
There are three main methods of provisioning; manual, automated, and self-service provisioning.
Manual Provisioning
This method involves administrators manually setting up systems, services, or user accounts. It requires direct intervention to configure hardware, install software, and manage access controls.
Advantages of Manual Provisioning
Customization. It allows for detailed customization of setups to meet specific requirements that automated tools might not accommodate.
Control. Administrators have full control over every step of the process, which can be crucial for compliance with strict regulatory standards.
Disadvantages of Manual Provisioning
- Labor Intensity. It is a time-consuming process that requires substantial manpower, making it less scalable for larger organizations or rapidly growing systems.
- Prone to Error. Human intervention increases the risk of errors, which can lead to security vulnerabilities or system failures.
- Cost. The labor-intensive nature of manual provisioning can lead to higher operational costs due to the ongoing need for skilled IT staff to manage and maintain systems.
- Slower Response Time. Manual interventions in system updates and problem-solving can delay organizational response times, affecting overall productivity and efficiency.
💡Suitable Scenarios for Manual Provisioning
- Small Organizations. Smaller entities with less complex systems might find manual provisioning manageable and cost-effective.
- Highly Specialized Requirements. Organizations with highly specialized needs that cannot be met by standard automated solutions may prefer manual setups to tailor their systems precisely.
- Regulated Industries. Certain sectors with stringent regulatory compliance requirements might opt for manual provisioning to ensure full control over every aspect of their IT environment.
💡Pro Tip → You can use ConductorOne’s Access Copilot to read, approve, and provision helpdesk access requests. Your IT team will never touch another access request ticket.
Self-Service Provisioning
This approach allows end-users to request and manage their own IT resources through a self-service portal. Users can apply for access to resources, software installations, and other services without involving the IT department.
Advantages of Self-Service Provisioning
Reduced IT Workload. It significantly reduces the routine workload of IT departments by automating the request and approval processes, allowing IT staff to focus on more complex tasks.
Faster Resource Allocation. The automation of approval workflows enables quicker provisioning of resources, reducing the waiting times typically associated with manual provisioning.
Enhanced Flexibility. Users can access resources on-demand, which is particularly beneficial in dynamic environments where needs can change rapidly.
Disadvantages of Self-Service Provisioning
- Potential for Misuse. If not properly managed, users might request more resources than needed or access inappropriate tools, leading to wasted resources or security risks.
- Complexity in Management. Setting up and maintaining a self-service portal with its underlying workflows can be complex and requires continuous updates and checks to align with evolving organizational policies.
💡Suitable Scenarios for Self-Service Provisioning
- Organizations with Flexible IT Needs. Companies where employees regularly need different tools or resources, such as in project-based industries or research and development, can benefit greatly from self-service provisioning.
💡Pro Tip → Enable self-service requests and enforce just-in-time access with ConductorOne.
Allow users to request access to any app, group, role, or permission with a self-service experience in Slack, CLI, or web app and automatic provisioning on approval.
Other Methods of Provisioning
Dynamic Provisioning
Dynamic provisioning systems adjust resources in real-time based on demand. This is often used in cloud environments where server capacity, storage, and networking can be scaled up or down automatically based on usage metrics. Dynamic provisioning helps optimize resource use and cost-efficiency.
Zero-Touch Provisioning (ZTP)
In zero-touch provisioning, devices are configured and ready for use the moment they connect to the network, without any manual setup required. This is particularly common in telecommunications and large enterprise environments, where new devices need to be deployed in large quantities with minimal human interaction.
Recommended → What is Zero Standing Privileges?
Just-in-Time Provisioning
Just-in-Time (JIT) provisioning involves creating user accounts and configuring access dynamically as needed. When a user accesses a service for the first time, their access rights and account settings are configured on-the-fly.
Secure your systems with ConductorOne — Book a demo.
How to Successfully Implement Provisioning in Your Organization
Implementing provisioning in an organization involves setting up systems and protocols to manage the allocation and management of resources across an IT infrastructure.
This includes everything from user access rights and data management to software deployment and hardware distribution.
The goal is to streamline operations, enhance security, and improve overall efficiency.
Step 1: Define the Requirements
- Identify Stakeholders. Begin by engaging with various stakeholders across the organization, including IT, HR, and department heads to gather comprehensive insights into the needs and challenges specific to each department.
- Determine Resources. Compile a detailed inventory of all resources that require provisioning. This list should include physical assets like computers and other hardware, as well as software licenses, network bandwidth, data storage, and any necessary third-party services.
- Define Access Levels. Develop a matrix that outlines access levels tailored to different roles and responsibilities within the organization. This step involves specifying the granularity of access controls. Ensure that you consider both vertical (management level) and horizontal (departmental) access distinctions. This should include who can access what levels of data, the type of data they can access, and under what circumstances.
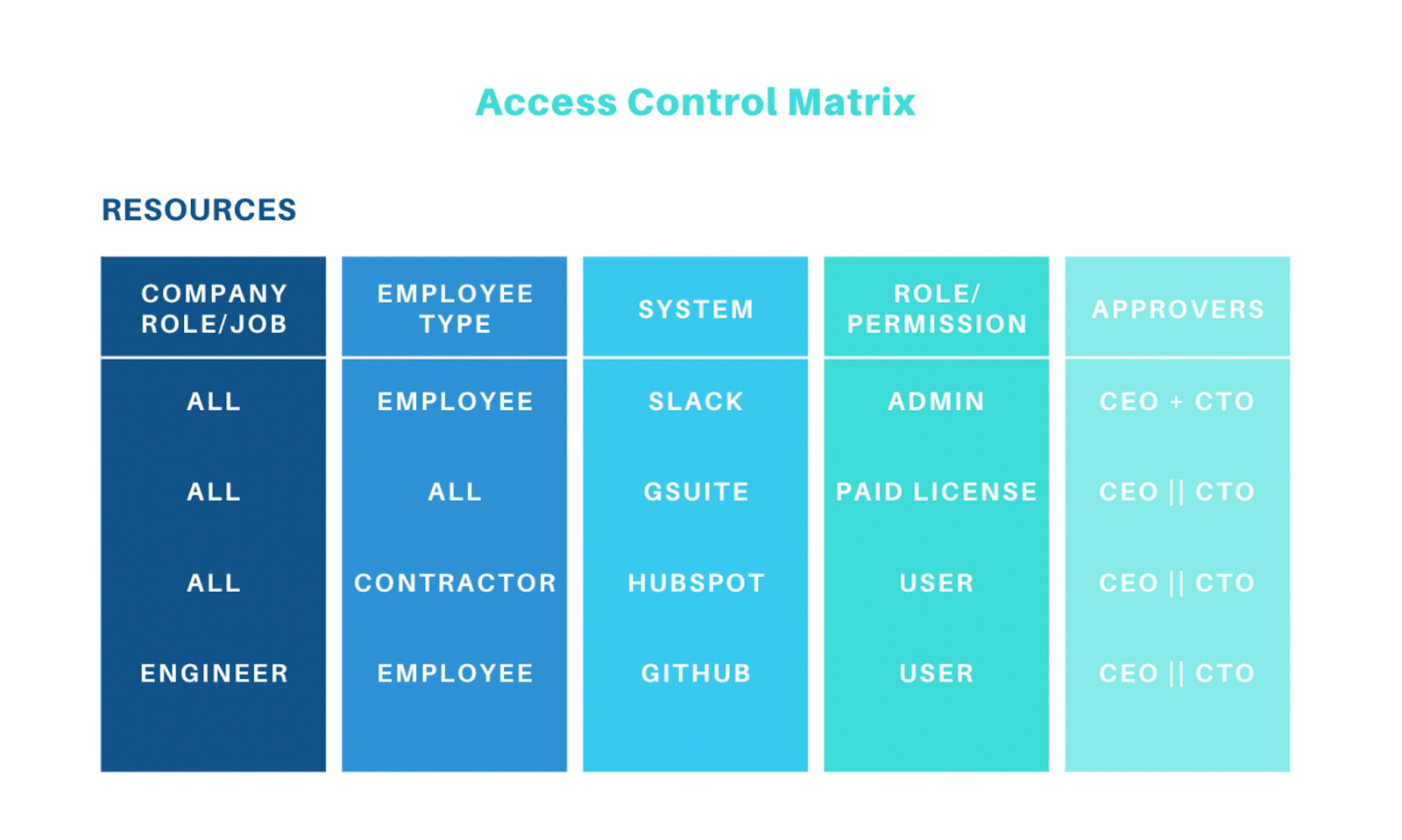
💡 Adopt a Role-Based Access Control (RBAC) strategy when defining access levels. This helps you simplify and manage user permissions by assigning access rights based on roles within the organization.
Step 2: Develop a Provisioning Policy
- Create Policy Documents. Draft detailed policy documents that outline the procedures for both provisioning and deprovisioning resources. These documents should clearly state the steps to be taken from the initial request to the final allocation of resources.
- Include specific timelines for how quickly resources should be allocated upon request to ensure efficiency and responsiveness.
- Establish Security Protocols. Implement security best practices to minimize security risks throughout the provisioning process. Key practices should include:
- Principle of Least Privilege. Ensure that individuals have access only to the resources necessary for their roles.
- Segregation of Duties (SoD). Divide critical functions among different people to reduce risk of error or inappropriate actions.
- Regular Access Reviews. Periodically review access rights to ensure they remain appropriate as roles and responsibilities evolve within the organization.
Related → Least Privilege Access: What You Need to Know
💡 To streamline the provisioning process and reduce human error, consider integrating automated workflow systems. These systems can help enforce your provisioning policies by automating the approval processes, tracking request statuses, and ensuring that all steps are completed in compliance with the established timelines and security protocols.
Step 3: Choose a Provisioning System
- Evaluate Software. Conductor a thorough evaluation of potential Identity Management (IdM) and Service Management (SM) systems. When assessing these systems, consider several key factors:
- Scalability. Ensure that the system can accommodate growth and handle increased demands as your organization expands.
- Multi-factor Authentication Support. Look for systems that support multi-factor authentication (MFA), which is crucial for enhancing security.
- Integration with Existing IT Infrastructure. Choose software that integrates seamlessly with your existing IT setup to avoid compatibility issues and streamline operations.
- Compliance with Regulatory Standards. Make sure the system meets all relevant regulatory requirements, which is essential for avoiding legal issues and maintaining trust.
- Select a System. After evaluating the options, choose a provisioning system that best meets your needs. The ideal system should offer:
- Robust Automation Capabilities. To reduce manual processes and improve efficiency.
- Flexible Integration APIs. These allow for easier customization and integration with other systems and applications in your IT environment.
Comprehensive Reporting and Analytics Tools. Essential for monitoring and improving the provisioning processes through data-driven insights.
💡 Before fully committing to a particular system, it’s advisable to conduct a pilot test with a select group of users from different departments. This testing phase will help you understand how well the system integrates with your current operations and meets your specific needs.
Step 4: Implement the Provisioning System
- System Setup. Deploy the selected provisioning system either on-premise or in the cloud. This decision should take into account several critical factors:
- Load Balancing. Ensure that the system is capable of distributing workload evenly across your servers to maintain optimal performance.
- Disaster Recovery. Implement disaster recovery plans that include regular backups and failover mechanisms to protect your data and maintain system availability during unexpected disruptions.
- High Availability Configurations. Set up your system to minimize downtime and ensure continuous service availability, even under high load or during partial system failures.
- Define Provisioning Workflows. Utilize automation to streamline the provisioning process. This can be achieved through:
- Scripting. Develop scripts to automate routine tasks such as user account creation, resource allocation, and permission assignments. Scripting can also help reduce manual errors and increase operational efficiency.
- Low-Code Platforms. Use low-code platforms to design and implement workflows. These platforms provide visual interfaces that simplify the automation workflows and can be used effectively by team members who may not have deep coding skills.
- Integrate with HR and IT Systems
- For HR. This allows you to automate provisioning workflows based on key employee lifecycle events such as onboarding, promotions, or even offboarding (termination).
- For IT Systems. Ensure the provisioning solution integrates with other internal systems including:
- Active Directory. For managing user identities and relationships within a network.
- ERP Systems. To align provisioning processes with business operations and resources.
- Network Management Tools. For overseeing and controlling network resources efficiently, ensuring that provisioning includes appropriate network access and monitoring capabilities.
💡 Use the built-in reporting and analytics tools of your provisioning system to track usage patterns, identify bottlenecks, and understand user behavior. Regular monitoring and analysis allow you to optimize workflows and system settings to better meet the dynamic needs of your organization.
Step 5: Training and Documentation
- Develop Training Materials. Create detailed user guides, FAQ documents, and training videos tailored to different user groups.
- Conduct Training Sessions. Organize targeted training sessions for different groups within your organization:
- For IT Administrators. Provide in-depth technical training that covers system management, troubleshooting, and security protocols.
- For End-Users. Hold sessions that focus on everyday tasks and functionalities they will encounter. Ensure these sessions include hands-on activities to help users gain practical experience and confidence in using the new system.
- Monitor and Adjust. Implement continuous monitoring tools to oversee system performance and user activities in real time. This could involve surveys, user forums, and direct feedback sessions.
💡 Implement a “train-the-trainer” approach. To do this, identify key individuals in different departments who can be trained intensively on the new system. These individuals can then act as in-house experts, providing training and support to their respective teams.
Provisioning Best Practices: The Ultimate Checklist
Automate Provisioning Processes
Automated tools can manage user accounts and permissions across various systems based on role-specific templates or policies, ensuring consistent access control. This helps eliminate manual errors, reduces the workload on IT staff, and speeds up the process of granting and revoking access.
Here’s how to implement this:
- Use Predefined Access Templates. These templates contain information on the access rights and privileges associated with each role within the organization. When a user is assigned a role, the provisioning system automatically applies the corresponding template, ensuring consistent and error-free access control.
- Utilize Conditional Access and Policy Management Feature. Modern provisioning tools are equipped with capabilities to implement conditional access policies. These policies can dictate access based on various conditions such as the user’s location, device security status, and network security level. This adds a layer of dynamic security that adjusts based on context.
- Create Self-Service Portals. Many organizations implement self-service portals that allow users to request additional access rights as needed. These portals are integrated with workflow engines that route the requests through an approval process. This self-service capability reduces administrative overhead and improves user satisfaction while maintaining control over access permissions.
💡Note → Now, just as important as provisioning, automated deprovisioning ensures that when an employee leaves the company or changes roles, their access rights are automatically revoked or adjusted accordingly. This helps prevent orphan accounts and reduces the risk of former employees accessing sensitive information.
Implement Role-Based Access Control (RBAC)
The first step in RBAC is to define clear roles within the organization. Each role should have associated responsibilities and permissions that are necessary to perform its functions. Roles should be as granular as possible to avoid excessive permissions that can lead to security vulnerabilities.
One way to do this is by using the “role-hierarchy” method — where permissions granted to a higher-level role are automatically inherited by the lower-level roles within the hierarchy. This reduces the complexity and potential errors in assigning permissions.
On the flip side, in more advanced RBAC systems, roles can be dynamically assigned based on context or attributes (a system often referred to as “Attribute-Based Access Control,” or “ABAC”).
For example, a user may gain additional temporary privileges based on the current task or lose certain privileges when accessing systems from an unsecured location.
Regularly Review and Update Access Permissions
You can conduct these reviews quarterly, bi-annually, or annually, depending on the organization’s size, turnover rate, and regulatory requirements.
The aim here is to ensure that permissions remain aligned with each user’s role, especially when job functions change due to promotions, transfers, or terminations.
To streamline the review process, it’s recommended to use automated tools. These solutions can flag permissions that deviate from predefined policies or that are excessive for certain roles.
Additionally, integrating access reviews with Identity Governance and Administration (IGA) solutions can help manage and enforce access policies. IGA systems provide tools for monitoring and managing identities and access rights across the entire organization, offering insights into potential risks and non-compliance issues.
Related → What is the Difference Between Identity Governance and SaaS Security Posture Management?
Use a Centralized Identity Management (CIM) System
A CIM system allows you to manage the user identities and their corresponding access rights across all systems from a single platform. This reduces the complexity of managing multiple systems independently and provides a single point of control for all user access.
To further streamline your CIM system, implement a Single Sign-On (SSO) solution to allow users to access multiple applications with one set of credentials. This approach improves user convenience and reduces the number of attack surfaces as users are less likely to resort to insecure practices like reusing passwords across systems.
Related → User Access Reviews: Process & Best Practices Checklist
💡Pro Tip → ConductorOne’s access controls allow you to create zero-touch, conditional, and multi-step approval policies. You can also remove access based on time, non-usage, or changed justification.
Ensure Compliance with Security Policies and Standards
Begin by thoroughly understanding the specific regulatory requirements that apply to your organization.
- GDPR for data protection in the EU,
- HIPAA for healthcare information in the U.S., and
- SOX for financial reporting. Map these regulations to specific controls and processes in your provisioning system.
Based on the regulatory requirements, develop comprehensive security policies that cover all aspects of the provisioning process. These policies should address user access levels, data handling, privacy measures, and audit controls. Also ensure these policies are well documented and accessible to relevant personnel.
Another key point here is using security controls that are tailored to specific roles within the organization. For example, roles that handle sensitive financial data may require stronger authentication measures and more stringent access controls than other roles. Regular SOX audits help verify that these controls are in place and functioning effectively to protect financial data and ensure compliance.
Secure the Provisioning Process
To properly secure your provisioning process, follow these security guidelines:
- Use Secure Protocols. Always use secure communication protocols such as HTTPS, SSH, and TLS for all data transmissions involved in the provisioning process. This ensures that data exchanged between systems and users is encrypted during transit, protecting it from interception or tampering.
- Encrypt Stored Credentials. Use industry-standard encryption algorithms such as AES (Advanced Encryption Standard) to encrypt data at rest. Ensure that encryption keys are also securely managed and rotated regularly.
- Deploy Robust Authentication Mechanism. This is to help verify the identity of users and systems involved in the provisioning process. This could include multi-factor authentication (MFA), biometric verification, and strong password policies.
- Secure APIs and Interfaces. Ensure that any APIs or interfaces used in the provisioning process are secure. This includes regular security assessments, using API gateways, and implementing rate limiting to prevent abuse.
- Log and Monitor All Provisioning Activities. This helps in detecting and responding to potential security incidents quickly. Ensure logs are protected, tamper-proof, and retained according to compliance requirements.
- Patch Management. Maintain a regular patch management process to ensure that all systems involved in the provisioning process are updated with the latest security patches. This reduces the risk of exploitation through known vulnerabilities.
- User Education and Awareness. Educate users involved in the provisioning process about security best practices, potential threats, and their responsibilities. Regular training can help in reducing human errors that could lead to security breaches.
- Develop an Incident Response Plan. This plan should outline clear procedures for containment, investigation, and recovery, along with communication strategies for notifying stakeholders.
💡Pro Tip → Conduct regular security audits and penetration testing of the provisioning systems to identify and remediate vulnerabilities. This should include both the software components and the underlying infrastructure.
Recommended → 7 Principles for Least Privilege Access Implementation.
Implement Provisioning Workflow with Approval Steps
Provisioning should ideally include a workflow that requires approval from appropriate managers or IT administrators before access is granted. This adds an extra layer of verification to prevent improper access provisioning and ensures accountability.
Here’s how to set this up:
- Define a clear workflow that outlines each step in the provisioning process, from request submission to final approval and provisioning. This workflow should detail the roles involved at each step and the criteria for moving from one step to the next.
- Customize the approval process based on the sensitivity and scope of the access rights being requested.
- For instance, accessing financial systems may require approvals from both IT security and finance department heads, whereas less sensitive systems may only require a direct supervisor’s approval.
- Integrate policy checks within the workflow so that certain conditions automatically trigger additional approval steps or preclude access until specific criteria are met. For example, access to high-risk data might require a secondary review by a compliance officer.
- Ensure that every step in the approval process is logged and that records are maintained for future audits. This includes capturing who approved what, when, and any comments or reasons provided during the approval process.
- Once approval is obtained, provisioning should be executed as per predefined templates and configurations to minimize errors. Automation can be used here to ensure that the approved permissions are accurately implemented in the relevant systems.
- Automated tools can also help route requests to the appropriate approvers, send reminders for pending approvals, and escalate delays automatically.
💡Pro Tip → ConductorOne helps you simplify onboarding and offboarding with automated multi-step provisioning and deprovisioning workflows, including delegated requests. Easily detect and revoke unused access, orphaned accounts, and deactivated users.
How to Complete Provisioning and Deprovisioning Tasks on ConductorOne
Complete a Provisioning Task
A request to grant new access has already been reviewed and approved. A provisioning task is now assigned to you because manual provisioning of the new access is required and you are a designated provisioner for the app.
Step 1: Receive a notification and go to the task
ConductorOne sends you notifications by email and Slack (if enabled) whenever a provisioning task is assigned to you. Make sure that notification emails can reach your inbox by adding no-reply@conductorone.com to your email contacts list.
Go to Interact with ConductorOne via Slack for instructions on setting up our Slack app.
- Log into ConductorOne by clicking the link in your email or Slack notification.
- If the link in your notification does not automatically direct you to the task, locate it by clicking on Requests in the Assignments section of the navigation panel. The badges next to each of these menu items show the number of tasks of each type currently awaiting your attention.
Step 2: Review the task and take action
Go to the Awaiting provisioning tab on the Requests page. Each line in the table is a provisioning task assigned to you.
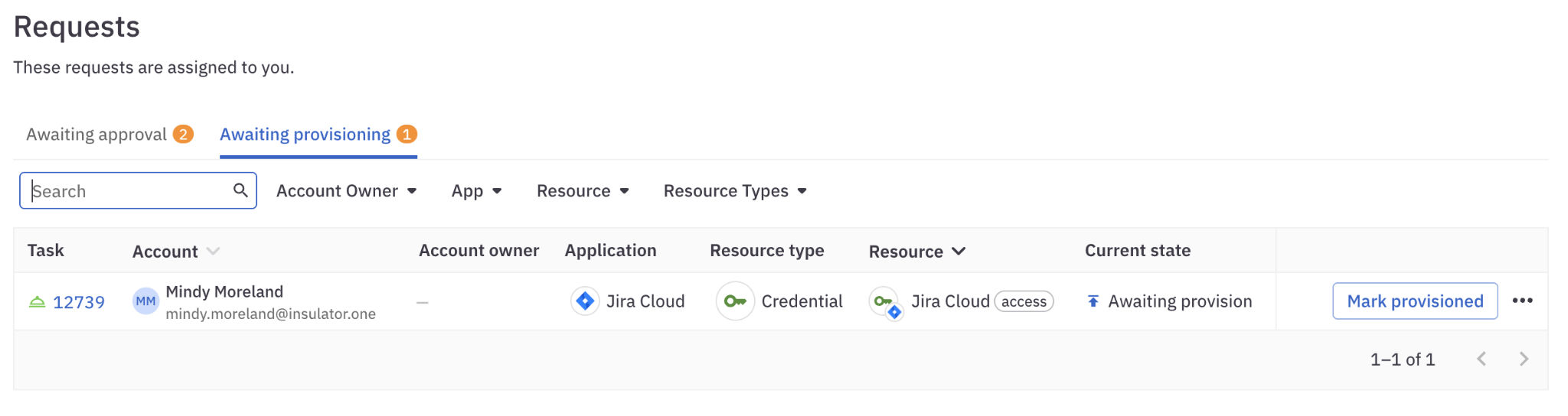
- Complete the deprovisioning process in the requested app and click to Mark deprovisioned. Click the more actions ( … ) menu for additional options, such as marking the deprovisioning as errored.
- If you need additional guidance or context, click the task number to open the task details page. Here you’ll find additional information to help you:
- If the ConductorOne admins at your company have provided any notes or instructions for how to complete the deprovisioning assignment, these are shown on the details page.
- The Comments section shows any notes other members of your organization have made about this task.
- The Task details section shows the task’s workflow, highlighting the role you play, and the policy being applied to this task. In this section you’ll also find controls to reassign the task, if reassignment is allowed.
Step 3: Repeat the process
Repeat these steps to complete each deprovisioning task assigned to you.
To take the same action on multiple tasks at once, select each task by clicking its checkbox, then select the action from the menu at the bottom left. You’ll be prompted to add a comment about your action, which is posted on each impacted task.
Click Completed tasks to see everything you’ve finished so far.
Complete a Deprovisioning Task
A request to revoke access has already been reviewed and approved. A deprovisioning task is now assigned to you because manual deprovisioning of the revoked access is required and you are a designated deprovisioner for the app.
Step 1: Receive a notification and go to the task
ConductorOne sends you notifications by email and Slack (if enabled) whenever a deprovisioning task is assigned to you. Make sure that notification emails can reach your inbox by adding no-reply@conductorone.com to your email contacts list.
Go to Interact with ConductorOne via Slack for instructions on setting up our Slack app.
- Log into ConductorOne by clicking the link in your email or Slack notification.
- If the link in your notification does not automatically direct you to the task, locate it by clicking on Revocations in the Assignments section of the navigation panel. The badges next to each of these menu items show the number of tasks of each type currently awaiting your attention.
Step 2: Review the task and take action
Go to the Awaiting deprovisioning tab on the Revocations page. Each line in the table is a deprovisioning task assigned to you.

- Complete the provisioning process in the requested app and click to Mark provisioned. Click the more actions ( … ) menu for additional options, such as marking the provisioning as errored.
- If you need additional guidance or context, click the task number to open the task’s details page. Here you’ll find additional information:
- If the ConductorOne admins at your company have provided any notes or instructions for how to complete the provisioning assignment, these are shown on the details page.
- The Comments section shows any notes other members of your organization have made about this task.
- The Task details section shows the task’s workflow, highlighting the role you play, and the policy being applied to this task. In this section you’ll also find controls to reassign the task, if reassignment is allowed.
Step 3: Repeat the process
Repeat these steps to complete each deprovisioning task assigned to you.
To take the same action on multiple tasks at once, select each task by clicking its checkbox, then select the action from the menu at the bottom left. You’ll be prompted to add a comment about your action, which is posted on each impacted task.
Click Completed tasks to see everything you’ve finished so far.
Reassign a Provisioning or Deprovisioning Task
In some cases, such as when an employee has moved to a new position in the company or when a colleague is out of the office on an extended vacation or leave, the task cannot be completed by its assigned reviewer and must be reassigned.
- In the task list, click Reassign. Alternatively, from a task’s details view, click Reassign in the Assigned to area.
- Select the new assignee and provide a reason for the reassignment.
The newly assigned reviewer will receive email and Slack (if enabled) notifications about their new task assignment.
Secure your systems with ConductorOne — Book a demo.




