Access governance is a critical component within identity and access management (IAM) that ensures that the right individuals have access to the appropriate resources at the right times and for the right reasons. It involves the processes and technologies that manage and regulate who has access to what information and systems within an organization.
1. ConductorOne — Best Next-Gen Identity Governance (IGA)
ConductorOne is a cloud-based identity security and access governance platform utilizing advanced automation and customizable workflows to streamline access management processes.
This includes automated onboarding and offboarding of users and orchestrating complex multi-step approval processes for access requests. ConductorOne seamlessly integrates and consolidates granular identity data from several sources, including cloud-based and on-premises applications, directories, and underlying infrastructure layers.
Some of ConductorOne’s advanced automation features include configuring auto-approvals for certain access requests based on predefined criteria and zero-touch deprovisioning for revoking access rights.
What Makes ConductorOne Different?
Compared to the traditional IGA solutions that are cumbersome, less flexible, and mostly designed for on-premises infrastructure, ConductorOne’s next-gen approach emphasizes:
Cloud-native design for better scalability and integration with cloud services.
User-friendly self-service capabilities to reduce IT overhead and improve user satisfaction.
AI and machine learning for enhanced security, anomaly detection, and automated decision-making.
Agile and continuous delivery model for rapid updates and feature rollouts.
💡Recommended Watch →
Key Features of ConductorOne’s Access Governance Solution
Unified Access Visibility and Control
ConductorOne offers a centralized platform for managing identity access across diverse environments, including cloud and on-premises applications, directories, and infrastructure.
This “single pane of glass” approach allows for comprehensive visibility and control over access rights, using powerful search and visualization tools to identify access insights and potential risks quickly.

In addition, ConductorOne automates access reviews and certification. It achieves this by leveraging machine learning for access modification suggestions and dormant account identification.
💡Benefit: This reduces manual review burdens and ensures access rights are promptly adjusted according to role changes or policy updates.
Automated Access Reviews and Compliance
To properly evaluate user permissions and access rights, ConductorOne implements a series of customizable workflows to automate the access review process — which includes:
- Multi-step reviewer policies, which enforce a rigorous review process by involving multiple stakeholders;
- Slack notifications, ensuring timely communication and actions;
- Auto approvals for low-risk access changes, minimizing administrative overhead, and
- Zero-touch deprovisioning for automatic removal of access rights, reducing the risk of unauthorized access.
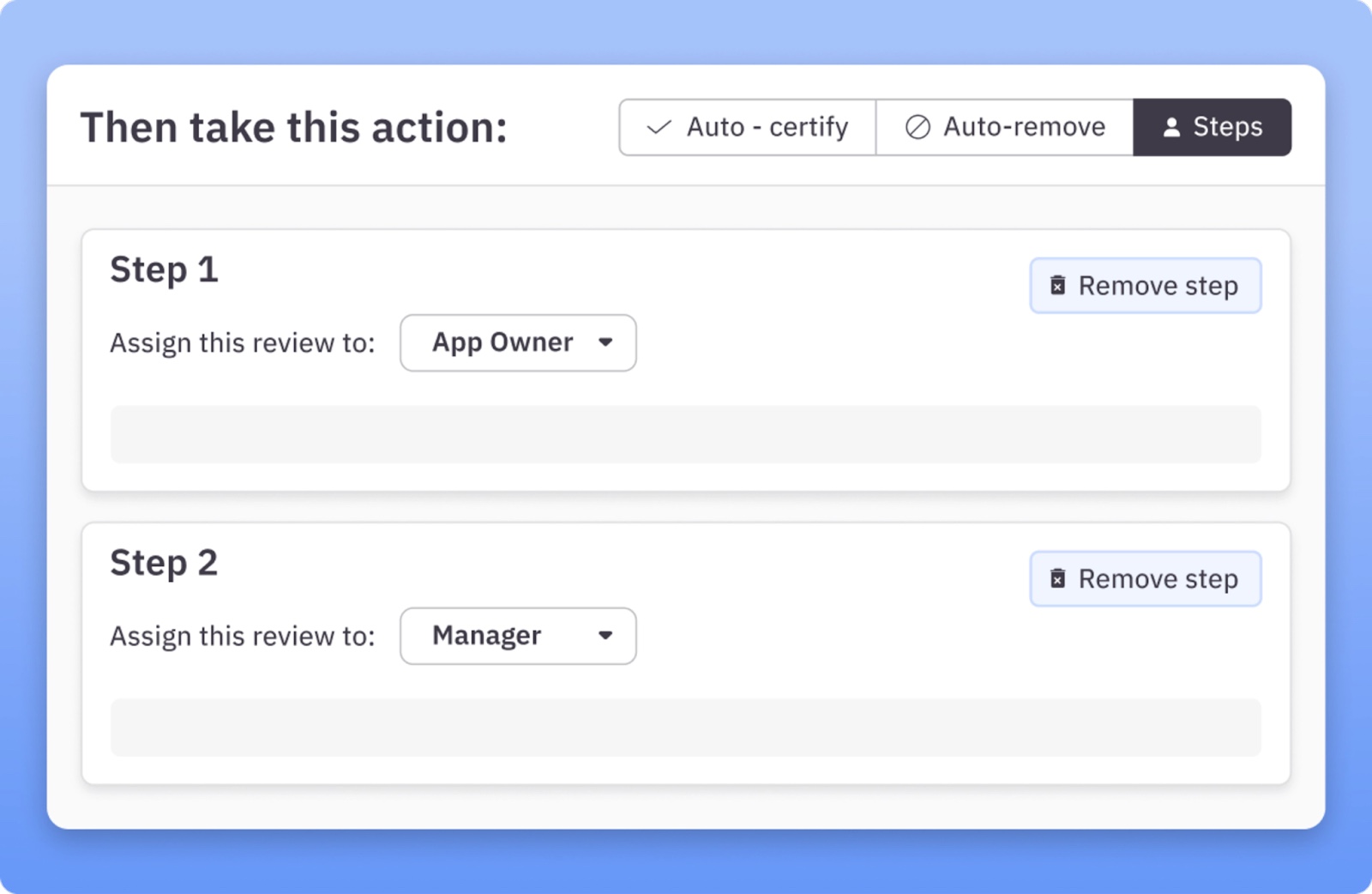
This automation also extends to compliance management, facilitating strict adherence to internal policies and external regulations. By automating routine compliance tasks, ConductorOne reduces the likelihood of human error and oversight, enabling a more consistent and efficient compliance posture.
💡Benefit: The system’s ability to automatically document and report on access reviews and changes aids in audit readiness, making it easier for organizations to demonstrate compliance with regulatory standards.
💡Must Watch →
Just-in-time (JIT) access
Implementing just-in-time (JIT) access through ConductorOne reduces risk linked with standing privileges by granting temporary access to resources only when required. This ensures that access permissions are only active during specified, need-based instances, automatically revoking these rights once the need expires.
ConductorOne’s JIT access capability enables you to enforce the Principle of Least Privilege (PoLP) — which states that users should be granted the minimum level of access necessary to complete their tasks (or job functions).
💡Benefit: Implementing JIT access reduces the attack vector for credential theft. Since elevated privileges are only available for a short window and are not constantly active, there’s no opportunity for hackers to steal and misuse these credentials.
Self-Service Access Requests
ConductorOne allows you to configure self-service access requests that enables users to independently request access to applications, groups, roles, or permissions.
This functionality is supported through various interfaces, including Slack, command line interface (CLI), and web app, allowing users to make flexible requests.
When a user submits an access request, it undergoes an automated approval workflow. The request is either approved or denied based on predefined criteria set by your organization’s IT or security team. This automation ensures that users can gain necessary access swiftly and efficiently without manual intervention for each request.
In the case where the system approves an access request, the user gets the required access rights they need to perform their job functions.
💡Benefit: Users gain quicker access to necessary resources, enhancing productivity, while IT and security teams experience reduced administrative burdens.
Recommended Watch →
AI-Powered Governance and Helpdesk Automation
ConductorOne utilizes AI to provide risk-based recommendations for access decisions, analyzing user roles, access patterns, and potential security risks to suggest the most appropriate access rights.
The platform also employs AI to automate helpdesk ticket processing through the Access Copilot feature. This feature can understand, approve, or deny access requests autonomously based on predefined policies and risk assessments.
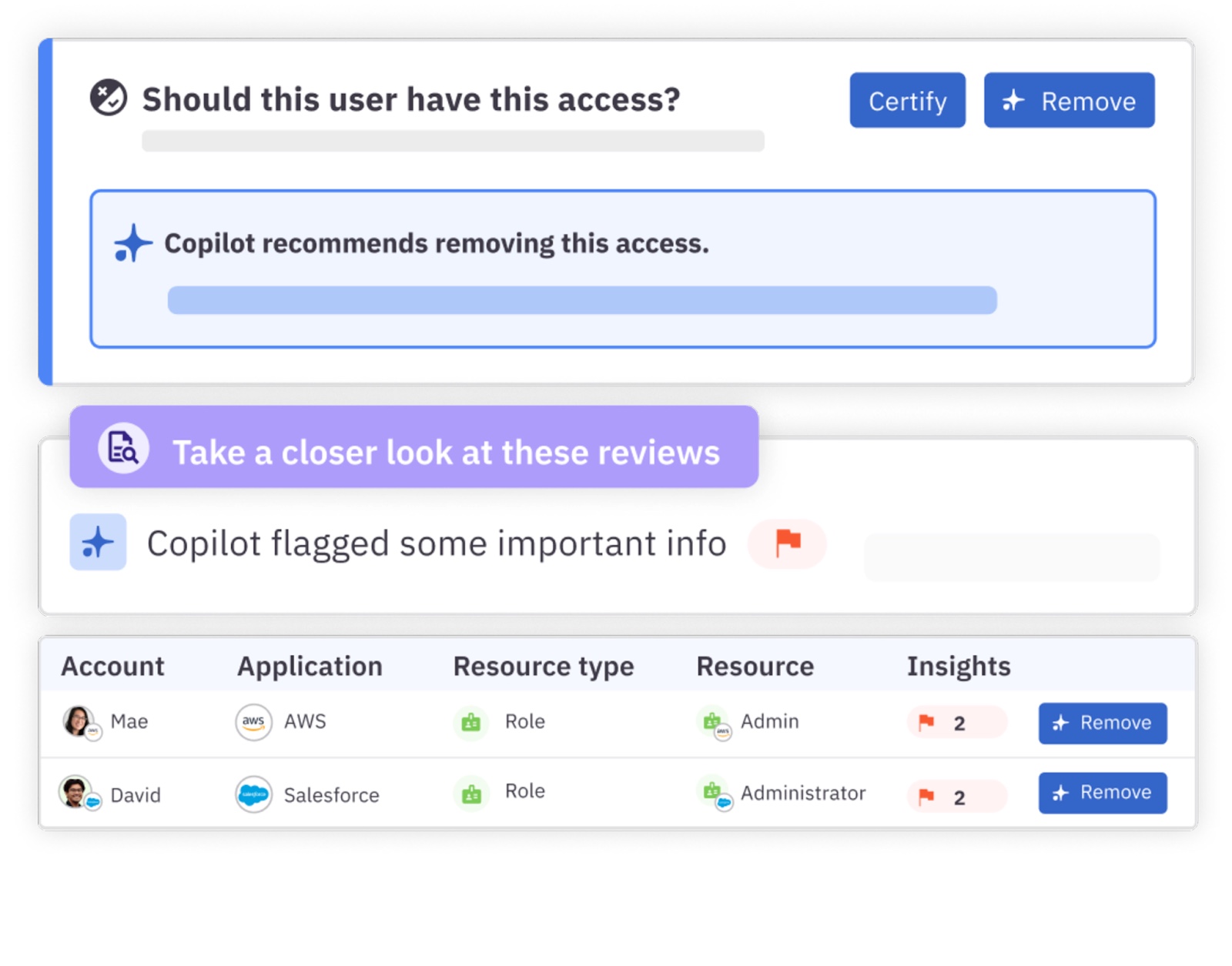
💡Benefit: With the implementation of AI, there’s a quicker resolution of access requests, which improves the organization’s security. This is possible because AI ensures that access rights are granted based on a thorough analysis of risk factors.
Developer-Friendly Configuration
ConductorOne supports configuration management via Terraform, enabling developers to define and provision the ConductorOne infrastructure as code. This method streamlines the setup and deployment processes.
ConductorOne provides a comprehensive API to enhance automation and customization. This API enables developers to integrate access management functionalities seamlessly into existing applications, scripts, or IT workflows.
Additionally, the platform offers command-line access for direct, scriptable interactions, allowing developers to request access or perform tasks without navigating through a graphical interface.
💡Benefit: Terraform configurations can be version-controlled along with application code. This allows teams to collaborate more effectively, track changes over time, and roll back to previous configurations if necessary, enhancing operational stability and team agility.
Seamless Integration via No-code Connectors
ConductorOne provides no-code connectors for integrating identity and user access data from HR systems, cloud platforms, SaaS, IaaS, on-premises, and homegrown applications into a single view.
Key functionality includes:
- Off-the-shelf, no-code setup that’s up and running in minutes.
- Real-time visibility into fine-grained permissions, roles, groups, resources, and more.
- Complete audit trail of access changes and usage.
- Easy lifecycle management with automatic provisioning and deprovisioning.
The platform also offers deep visibility into roles, groups, and usage data, quickly contextualizing access relationships across applications. It achieves this in three steps:
Step 1: Fully automated. Real-time access lifecycle management using pre-built connectors.
Step 2: S3 bucket. Semi-automated upload best for existing data extraction tooling.
Step 3: File upload. Files manually uploaded directly for processing.
💡Benefit: The unified view of identity and access across the organization eliminates silos and makes it easier to manage user access properly.
💡Pro Tip → For organizations using Okta as their centralized identity provider, ConductorOne enables enforcement of the principle of least privilege with time-based access controls, just-in-time access provisioning, and easy-to-use access reviews.
Baton for Infrastructure Access Audit
A significant part of ConductorOne’s offering includes Baton, an open-source framework for connectors. Baton allows for customization of connectors to extract, normalize, and interact with identity and access data.
The tool follows a simple data model consisting of resources, entitlements, and grants to map access rights across apps and infrastructure. It provides organizations with a real-time snapshot of access privileges for improved security and compliance.
Baton comprises three major components:
- The Baton CLI. A command line interface that provides a set of commands to extract, compare, and explore identity, resource, and permission data in an app.
- The Baton SDK. A toolkit that makes building a connector for any application seamless.
- Baton Connectors. These pre-built and supported integrations work with common SaaS and IaaS apps to sync identity and permission data.

💡Pro Tip → With ConductorOne, you can instantly generate detailed reports on user access reviews, compliance status, and deprovisioning actions with a single click.
Why Do Customers Choose ConductorOne?
Simple — Security and IT teams love ConductorOne for identity governance and least privilege access controls.
Users on G2 also agree with this:
- “Simplest access management on Earth.”
- “UAR automation could never get easier.”
- “What used to take months now takes days for us with C1.”
- “Access management & reviews reinvented.”
- “Identity management made easy.”

💡Case Study → Read How System1 manages disparate systems after M&A activity and streamlined SOX audits.
2. Okta Identity Governance (OIG)
Okta Identity Governance is a unified identity management and governance solution designed to help organizations manage user identities and access rights across various applications and services.
This solution is part of Okta’s broader identity and access management (IAM) offerings (Okta Lifecycle Management and Workflows products), focusing on enhancing security, compliance, and operational efficiency.

How Okta Works
- Okta Lifecycle Management delivers integrated solutions linking HR and IT systems, enabling seamless synchronization of employee information and their access to IT applications. This system ensures that as employees join, transition within, or exit the organization, their access to applications and resources is automatically managed—assigned, updated, or removed.
- Okta Workflows offers the flexibility and customization options necessary to address the complex identity governance requirements specific to your organization. It allows for the easy automation of identity-related tasks on a large scale without needing to code. With Okta, anyone in your organization can develop innovative identity management solutions using simple if-this-then-that logic, leveraging Okta’s extensive library of pre-built connectors and connecting to any available public API.
Advantages
- Automated Lifecycle Management. OIG automates the entire lifecycle of user identities and access rights, from onboarding to offboarding. It integrates with HR systems (like Workday and SuccessFactors) for automated user account creation, role assignment, and access provisioning based on job roles, changes, or departures.
- Access Request and Approval Workflows. It offers a self-service portal where users can request access to resources, and designated approvers can approve or deny these requests based on policies. This highly configurable process can incorporate multi-level approval workflows, ensuring access is granted according to organizational policies and compliance requirements.
- Access Certification and Review. OIG enables organizations to conduct regular access reviews and certifications to ensure compliance with internal policies and external regulations. Reviewers can verify or revoke user access rights, helping to minimize the risk of excessive or outdated privileges.
- Policy and Role Management. It provides tools for defining and managing access policies and roles, allowing for granular control over who has access to what resources. Policies can be based on attributes like job function, department, or location, facilitating least privilege access enforcement.
- Advanced Analytics and Reporting. Okta Identity Governance offers comprehensive analytics and reporting capabilities, enabling organizations to monitor access patterns, identify potential security risks, and ensure compliance with audit requirements. Reports can be customized and automated, providing insights into access anomalies, inactive accounts, and segregation of duties violations.
Disadvantages
- Device Change Challenges. When changing devices, users face severe access issues, known as the “Okta death loop,” which can potentially lead to locked-out situations without clear workarounds [*].
- Limited AD Integration Flexibility. Integrating non-AD user repositories with Okta requires additional development, indicating limited out-of-the-box flexibility [*].
- Frequent & Unnecessary Verification. The need for repeated login verifications on mobile devices disrupts user productivity, particularly during critical presentations or demos [*].
- Remote Access Restrictions. Okta’s security measures can sometimes prevent access to work accounts from non-company networks, necessitating physical presence or support intervention, which can be inconvenient [*].
Pricing
- Light: $9 per user, per month up to 50 flows
- Medium: $10 per user per month up to 150 flows
- Unlimited: $11 per user per month for unlimited flows
3. StrongDM
StrongDM is an infrastructure access platform that provides secure, auditable, and easy-to-manage access to databases, servers, clusters, and web applications. It acts as a unified control plane, streamlining how users connect to essential infrastructure without requiring traditional VPNs, SSH keys, or database credentials.
The platform uses a protocol-aware proxy architecture to manage connections to various resources.
For example, when a user attempts to access a resource, StrongDM authenticates the user against the organization’s identity provider (e.g., Okta, Active Directory) and then checks the user’s permissions. If authorized, StrongDM dynamically generates the necessary credentials and establishes a secure connection to the target resource, all without exposing those credentials to the user. This process ensures that access is secure and transparent, minimizing the risk of credential leakage or unauthorized access.
Advantages
- Credential Leasing. StrongDM adds credentials to the target database or server during the final step, ensuring users never access sensitive credentials directly. Credentials are unlocked at runtime with a “dual-key” system, requiring a valid proxy and user session for decryption. Access to databases or servers is granted through roles or temporary permissions using Leased Credentials.
- Secret Store. Uses AWS Key Management Service (KMS) for encryption, specifically authenticated encryption with associated data (AEAD). Credential activities are recorded in a secure audit log managed by a separate AWS account.
- Admin UI. Allows admins to manage access, roles, logs, replays, infrastructure, and settings. End users can only download the StrongDM Desktop Application and CLI, and access documentation through it.
- Strong Vault. This is an encrypted repository for secrets, keys, and credentials. It ensures the security of these items, recording decryption events in a secure audit log under a separate AWS account. Though it uses AWS, StrongDM supports various vault options like Azure Key Vault, CyberArk (Conjur and Digital Vault), Delinea Secrets Server, Hashicorp Vault, GCP Secrets Manager, and Amazon Secrets Manager.
Disadvantages
- Database Selection Delays and UX Overhaul. Users experience delays in database accessibility post-approval and challenges adapting to significant UX changes, alongside cumbersome web-based login processes likely due to SSO limitations on certain platforms [*].
- Automation and Discovery Limitations. Requires manual creation of automation and scripts, for instance, registration, lacking autodiscovery and cloud visibility, with agent stability issues and API-only support for certain options [*].
Pricing
- Essentials: $70 per user/month (annual plan only).
- Enterprise: Contact sales.
- GovCloud: Contact sales.
4. Netwrix Data Access Governance
Netwrix Data Access Governance is an extension of the broader Netwrix cybersecurity framework, specifically developed to enhance the control and monitoring of access to sensitive and critical data across an organization’s IT environment. This includes files, documents, and emails stored across various data repositories such as file servers, SharePoint sites, and cloud storage services.
Advantages
- Lockdown Endpoint Privilege. Prevents the risk of malware, ransomware, and noncompliance by delegating only the permissions standard users need, not local admin rights.
- Zero-Standing Privilege. Minimizes attack surface by replacing standing privileges with on-demand accounts and ensures just-in-time (JIT) access is granted across all platforms, including databases.
- Local Administrator Security. This feature shuts down attack vectors while still enabling users to perform specific tasks that require elevated privileges on their machines by replacing all-or-nothing local Administrator rights with granular privilege elevation.
Disadvantages
- Delayed Support Response. Resolving issues with support can be slow, often taking days to weeks, due to reliance on email communication and the need to schedule support sessions within limited availability [*].
- Complex Report Setup. Setting up reports can be challenging due to confusing instructions, although support can guide the process and address related issues [*].
Pricing
- Netwrix doesn’t offer transparent pricing, so you’d need to content them directly.
5. SecurEnds
SecurEnds is a cloud-based security and compliance solution specializing in Credential Entitlement Management (CEM).
It aims to help organizations manage and audit user credentials and entitlements across various cloud and on-premises systems. The platform addresses critical identity and access management (IAM) aspects, including access reviews, identity governance, and compliance reporting.
How SecurEnds Works
- Loading of Employee Data. Employee information from HR Management Systems (e.g., ADP, Ultipro, Paycom, Workday, etc) is imported via built-in connectors or files.
- Identity Integration. Connectors retrieve identities from various sources, including enterprise applications (Active Directory, Salesforce), databases (SQL Server, MySQL), and cloud platforms (AWS, Azure).
- Access Review Setup. Application owners or managers organize periodic or one-off access reviews based on roles or attributes, tracking changes through delta campaigns.
- Analytics & Governance. An AI/ML module analyzes access for irregularities, focusing on risk profiles and excessive privileges. The module can filter by campaigns, applications, or entitlements.
Advantages
- Unified Identity Repository. A centralized database infrastructure designed to aggregate and manage digital identities across the entire organizational ecosystem. This repository is a singular reference point for all identity-related information, facilitating streamlined access control, identity verification, and user management processes.
- Identity-Centric Mind Map Visualization. This feature utilizes an advanced query and filtering mechanism that allows stakeholders to refine the visualization based on specific criteria, such as user identity, application systems, or entitlement categories.
- Centralized Audit Trail Management System. This feature integrates advanced remediation capabilities directly within the audit trail framework, leveraging ITSM principles to streamline resolving identified issues or security vulnerabilities.
- Role-Based Review Allocation and Execution. This feature intelligently assigns review tasks to the appropriate reviewers based on their organizational role, domain of responsibility, or specific expertise.
- For instance — direct managers are primarily responsible for reviewing the access rights of their immediate subordinates; entitlement custodians oversee the distribution and proper usage of specific entitlements; application managers focus on access related to the applications under their purview; and ad-hoc reviewers are engaged for specialized or exceptional review cases.
Disadvantages
- Limited Customization. There have been frequent technical problems and insufficient testing, and there is no option to customize notification delivery, limited variables for email configuration, and no direct way to review the separation of duties [*].
- Poor Alerting and Intelligence. There’s room for improvement in alerting mechanisms and adding identity intelligence for advanced use, although it’s not seen as an immediate necessity [*].
- Complex Endpoint Setup. Configuring endpoints as the source for employee/manager relationships can be complex and challenging [*].
Pricing
- Contact SecurEnds for more information.
6. Solarwinds Access Right Manager (ARM)
SolarWinds Access Rights Manager (ARM) is an access rights management tool that monitors, analyzes, and manages user permissions.
It provides a graphical representation of access rights across the network, making it easier to identify who has access to sensitive data, how they received that access, and whether their access level is appropriate for their role within the organization. This visualization aids in quickly spotting and rectifying any permissions that may expose the organization to risk.
Advantages
- Active Directory and Group Policy Integration. ARM deeply integrates with Active Directory and Group Policy Objects (GPOs), providing administrators with the tools to manage user accounts and access rights from a centralized location. This integration also extends to automating and enforcing access policies across the organization.
- Decentralized Access Rights Management via Self-Service Portal. The ARM framework decentralizes the management of user access rights by allowing data owners to directly oversee and delegate access to the resources under their control.
- Granular Data Collection. ARM’s auditing system captures and analyzes user activities, permission changes, access logs, and system configurations within different environments. These include Active Directory, various file server architectures (such as Windows Server, EMC, and NetApp storage solutions), SharePoint and SharePoint Online, Exchange and Exchange Online, Microsoft Teams, OneDrive, and SAP/R3 environments.
Disadvantages
- Limitations in Organization and Automation. Inability to create organizational units in AD, complexity in using JSON for automation and templates, and issues with automatic deletion from recertification [*].
- Access and Support Concerns. Self-service portal access levels should vary by need, with deficiencies in support quality noted [*].
- User Template Creation Challenges. The process requires third-party add-ons, highlighting a need for direct ARM integration to create user account templates [*].
- Licensing and Functionality Issues with SolarWinds. The transition to the SolarWinds licensing model has been described as a nightmare, with difficulties in understanding entitlements and current system unusability due to login errors despite recent license renewal [*].
Pricing
- SolarWinds ARM pricing is not disclosed. However, there are flexible licensing options to use the service.
7. Evidian IGA
Evidian Identity Governance and Administration (IGA) integrates a robust set of governance tools designed to streamline the oversight of identity-related risks and compliance with regulatory standards such as GDPR, HIPAA, SOX, and more.
In addition, Evidian IGA offers robust tools for defining, enforcing, and reviewing access policies and controls. It allows organizations to implement role-based access control (RBAC), segregation of duties (SoD) policies, and least privilege access, minimizing the risk of unauthorized access or data breaches.
Advantages
- Advanced Privileged Account Management Integration. Evidian IGA ensures a high degree of interoperability and integration with top market solutions, including PAM platforms like CyberArk and Wallix and ITSSM tools such as ServiceNow.
- Unified Audit Event Consolidation. The solution is designed to aggregate audit events from various sources into a centralized database, leveraging the integration capabilities of Enterprise Single Sign-On (SSO) and Web Access Manager.
- Workflow and Policy Engine. The solution automates the entire lifecycle of user identities, from creation through modification to deletion. This automation extends to the provisioning and deprovisioning access rights, ensuring that users have access to the necessary resources based on their roles and responsibilities within the organization.
Disadvantages
- Storage and Security Concerns. Additional space is needed for user, roles, and permissions databases, including Active Directory roles. Storing this data on the public cloud may introduce security risks [*].
- Usability and Performance Challenges. The product has a steep learning curve and an outdated user interface, with underdeveloped reporting features and unclear error messages complicating debugging. Performance issues arise with high-volume provisioning [*].
Pricing
- Contact Evidian for more information.
8. SAP Access Control and Governance
SAP Access Control and Governance, part of SAP’s broader GRC (Governance, Risk, and Compliance) portfolio, is designed to streamline access rights management and ensure compliance across SAP environments (including SAP ERP and S/4HANA).
Additionally, SAP Access Control utilizes a powerful business rule framework that allows organizations to define and enforce their access policies. This framework supports the customization of SoD rules and risk analysis criteria, enabling businesses to tailor the solution to their specific risk management and compliance needs.
Advantages
- Controlled Access via Firefighter IDs (FFIDs). The solution employs the FFIDs to grant temporary and highly restricted privileges to designated users. FFIDs enable swift response to critical incidents while maintaining a comprehensive audit trail of the activities performed under these temporary privileges. This method ensures that all actions taken during the emergency access period are traceable, auditable, and aligned with internal security policies and compliance requirements.
- Enhanced System interaction Tracking. SAP Access Control captures and syncs information on Web Dynpro components and Business Server Page (BSP) applications within the system.
- Asynchronous Risk Analysis Process. This feature introduces a sophisticated mechanism for conducting risk analysis asynchronously at two critical junctures within the access request workflow — firstly at the initial point of request submission, and secondly, at the stage of request approval. This dual-phase risk evaluation approach ensures that risk assessments are timely and contextually relevant to each stage of the access management process.
Disadvantages
- Complex Customization and Outdated Interface. The software’s high customization capabilities make it difficult to set up and use, and its interface is outdated [*].
- Account Management and Navigation Challenges. Account recovery requires significant time with administrator assistance, and distinguishing between servers is complicated within an outdated platform appearance [*].
- Third-Party Integration and Log Limitations. Integrating external systems is challenging, with a steep learning curve and limited log details complicating customization and troubleshooting [*].
- Connector Limitations and Research Needs. The absence of startup connectors and the need for improvement in SAP IDM connectors highlight areas for development and research [*].
- Complexity and Lock-in Concerns. SAP IdM’s complexity and cost make it challenging to learn and use, particularly for small businesses, with significant implications for changing systems due to lock-in, performance issues with large data sets, and the high cost [*].
Pricing
- Contact SAP Access Control for more information.
9. Zluri
Zluri is a unified access management solution providing tools for IT teams to discover, manage, optimize, and secure SaaS applications throughout the organization. It uses advanced techniques to catalog all SaaS applications, including unauthorized ones (shadow IT), offering complete visibility and improved management of the SaaS stack.
Zluri’s architecture utilizes AWS Web Application Firewalls, subnets, and security gateways to restrict data flow. Specific AWS rules facilitate data movement while also encrypting data on disk for enhanced security. Communications between the application and users are secured through HTTPS and TLS v1.2 or higher, and authentication is handled by Auth0, incorporating SSO options from Google, Microsoft Office 365, and others.
Furthermore, AWS load balancers manage incoming traffic, and the AWS firewall blocks unauthorized and malicious traffic, including DDoS and SQL injection attacks. Traffic authentication is achieved using JSON Web Tokens (JWT), and monitoring is conducted via internal load balancers. External connections are inspected through a NAT gateway.
Advantages
- Secure Data Encryption and Backup Policies. All data stored within Zluri’s platform is encrypted, protecting sensitive information against unauthorized access. Furthermore, the platform maintains a data backup for up to 60 days, providing an additional layer of data security and recovery in the event of data loss or system failure.
- SAML-Based Authentication Integration. Zluri supports the integration of Security Assertion Markup Language (SAML)-based authentication mechanisms, enabling seamless and secure access to the Zluri platform using credentials managed by widely recognized Identity Providers (IdPs) such as Okta, Microsoft Azure, and G Suite.
- Pre-configured Roles for Granular Access Control. Zluri is equipped with various pre-configured roles defining distinct access permissions levels within the platform. These roles are designed to facilitate granular access control, allowing organizations to tailor user access based on specific needs and responsibilities. Users can be assigned roles that grant them access to manage financial data, specific applications, or user management tasks, among other things.
Disadvantages
- Data Accuracy and Integration Challenges. User data from multiple sources can be inaccurate, and difficulties arise from incomplete application integrations in Zuri’s catalog alongside outdated integration instructions [*].
- Information Overload and Usability Issues. The app presents overwhelming information, leading to navigation difficulties, a challenging onboarding process, and areas needing quality assurance and additional app integrations [*].
- Direct Transaction Access Desired. Users would benefit from the ability to access transactions in Netsuite directly via integration, indicating a need for improved integration features [*].
Pricing
- Contact Zluri for more information.
10. Zilla Security
Zilla Security is a modern cloud security and compliance platform designed to help organizations secure their cloud environments and ensure compliance with various regulatory standards. It provides comprehensive visibility into cloud infrastructure, applications, and data across multiple cloud service providers (AWS, Azure, and Google Cloud Platform).
The platform supports automated compliance assessments against industry standards and regulatory frameworks, such as GDPR, HIPAA, PCI DSS, and SOC 2. Zilla Security generates detailed compliance reports, making it easier for organizations to demonstrate compliance to auditors and stakeholders.
Advantages
- Automated User Account and Permission Retrieval. ZUS leverages advanced robotic process automation (RPA) techniques to automate the extraction of user accounts and their associated permissions from integrated applications.
- Secure Data Import. Zilla supports the secure importation of CSV files through FTP connections encrypted using SSL/TLS protocols from legacy systems and on-premises applications. This feature ensures safe data transmission, protecting sensitive account and permission information from potential interception or unauthorized access during import.
- No-Code Integration. The platform offers a no-code solution for integrating with most systems that provide support for REST APIs, covering various applications related to accounts, permissions, and security settings.
Disadvantages
- Decentralization Challenges with Zilla. In small, decentralized organizations, compiling disparate departmental accounts into Zilla is time-consuming, highlighting challenges in managing non-centralized relationships [*].
- Complex Identity Environment Issues. Navigating complex identity environments with multi-tenant, multi-domain setups and frequent identity changes often requires manual account cleanup, indicating limitations in automatic user-to-identity matching [*].
- Reporting Flexibility Limitations. Zilla lacks the capability for users to customize existing reports or create custom reports, restricting analytical flexibility [*].
Pricing
- Contact Zilla Security for more information.
11. SailPoint
SailPoint provides robust identity governance capabilities, enabling organizations to define and enforce access policies, conduct access reviews, and manage roles and entitlements. It also automates the entire lifecycle of user access, from onboarding to offboarding, streamlining the process of granting and revoking access rights.
Regarding system architecture, SailPoint is built on a scalable framework that can accommodate the growing identity needs of large enterprises. It supports a broad range of applications and data on-premises and in the cloud. With its AI and Machine Learning capabilities, SailPoint can detect anomalous access patterns and potential security threats, providing recommendations for strengthening identity security in your organization.
Advantages
- Granular Analysis. This advanced feature provides organizations with deep visibility into and detailed analysis of user access histories, enabling them to go beyond mere access control to understand exactly how access rights are being utilized.
- Access Review Automation. SailPoint’s Access Risk Management platform and Identity Network (IDN) offer a robust solution for automating the entire spectrum of access review workflows from initiation to completion.
- Mobile Approval for Access Requests. Access Risk Management enables the approval of emergency access requests via mobile devices to enhance flexibility and ensure that they are addressed without delay.
- Pre-approved Super-User Profiles. SailPoint offers quick configuring and utilizing pre-approved super-user profiles to expedite the provisioning process during emergencies.
Disadvantages
- Poor Customer Support. The product’s complexity leads to bugs and cache problems, necessitating lengthy support processes with SailPoint, which sometimes fail to resolve the issues effectively [*].
- Cache Issues and Save Failures. Working on rules or workflows is hindered by cache problems, especially when working across multiple tabs and experiencing delays in saving, leading to unreflected changes [*].
- Limited Customization in IdentityNow. IdentityNow offers minimal customization options, creating bottlenecks and lacking out-of-the-box solutions for certain requirements [*].
- Delay Challenges in IdentityIQ. IdentityIQ’s task-based architecture introduces delays in processing updates from authoritative sources, making it difficult to maintain real-time operations in environments with updates from multiple sources daily [*].
- Cloud Version Limitations. The cloud version of IdentityNow offers less customization than the on-premises version, and customizable connector views are needed to better serve different customer use cases [*].
- Lack of Traditional Governance Features. IdentityNow’s SaaS platform misses some traditional identity governance capabilities, particularly in generating or consuming CSV files, and lacks features in on-premise platforms [*].
Pricing
- Contact SailPoint for more information.
Factors To Consider When Choosing Access Governance Solutions
When evaluating access governance software, it is important to conduct a thorough needs assessment and pilot test with critical systems. This ensures that the chosen solution meets the organization’s technical requirements and business objectives.
Compatibility with Existing IT Infrastructure
- Integration Points. The software should seamlessly integrate with various systems, including on-premises and cloud applications, databases, and network infrastructure. Look for support for standard protocols like LDAP for directory services, SAML and OAuth for web single sign-on (SSO), and SCIM for user provisioning
- Directory Services. It is crucial that user identity management be compatible with existing directory services (e.g., Active Directory, Azure AD).
- Synchronization. The software should be capable of synchronizing with multiple directory services, ensuring that changes in user status (e.g., new hires, departures, role changes) are automatically reflected in access permissions.
- Federation. The access governance software should support identity federation for organizations using multiple directory services or hybrid (on-premises and cloud) environments. This allows for a seamless user experience and centralized management of access policies across disparate systems.
- Legacy Systems. Consider how well the software can integrate with legacy systems, which may not support modern authentication and integration standards. This might require custom connectors or middleware.
Scalability to Accommodate Organizational Growth
- Architectural Design. The software’s architecture should support horizontal scaling to handle increasing loads, potentially through cloud-based services or clustering techniques.
- Microservices Architecture. A microservices-based architecture can enhance scalability by allowing individual software components to scale independently based on demand.
- Cloud-native Features. For SaaS or cloud-based deployments, look for cloud-native features such as auto-scaling, load balancing, and containerization (e.g., Kubernetes support), which can dynamically adjust resources to meet workload demands.
- Performance Metrics. Request or conduct benchmark tests that mimic your organization’s expected load and usage patterns. Features like caching, query optimization, and efficient data storage can significantly impact performance.
- License and Cost Model. The licensing model should be flexible to accommodate growth without exorbitant costs. Per-user licensing or tiered models can significantly impact the total cost of ownership as your organization expands.
User-friendliness and Ease of Deployment
- Interface and Navigation. The user interface should be intuitive for both administrators and end-users. Look for a clean, straightforward design that simplifies complex tasks, such as requesting access or reviewing access rights.
- Training and Documentation. Comprehensive documentation and training resources are essential to reduce the learning curve and ensure successful adoption. Evaluate the quality and accessibility of user guides, online training, and support forums.
- Deployment Options. Consider whether the software offers flexible deployment options that match your IT strategy.
- Containerization and Orchestration. Support for containerized deployment options, like Docker containers managed by Kubernetes, can simplify software deployment, scaling, and management across different environments.
- Hybrid and Multi-cloud Support. Deploying in hybrid or multi-cloud environments offers flexibility in leveraging existing on-premises infrastructure alongside public clouds for scalability and resilience.
Comprehensive Reporting and Analytics Capabilities
Audit Trails and History. The software should provide detailed audit logs and history for all access-related activities. This is critical for compliance with regulations (e.g., GDPR, HIPAA) and internal audits.
💡Pro Tip → Opt for solutions that maintain immutable logs that cannot be altered or deleted. This is critical for forensic analysis and compliance audits.
- Analytics Tools. Look for built-in analytics tools that offer insights into access patterns, potential security risks, and compliance posture. The ability to customize reports and set up automated alerts for unusual activities is highly beneficial.
- Data Visualization. Advanced data visualization features can help quickly identify issues or trends related to access governance. Dashboards and interactive charts make it easier for stakeholders to understand the access landscape.
Support and Customer Service Offerings
- Service Level Agreements (SLAs). Detailed SLAs that specify response times, resolution times, and availability guarantees can assure timely and effective support.
- Expertise and Resources. Assess the support team’s expertise and the availability of resources such as technical whitepapers, troubleshooting guides, and best practice documents.
- Software Updates and Maintenance. Understand the frequency of updates and how they are applied. Look for solutions offering zero-downtime updates or scheduling updates during off-peak hours to minimize disruption.
ConductorOne — Simplify Access Control with Modern IGA
ConductorOne offers a modern Identity Governance (IGA) solution to simplify access control across complex environments. With ConductorOne, organizations can gain visibility, automate access reviews and reporting, manage the identity lifecycle, and enforce policy-driven access controls all from a single platform.
- Automated quarterly user access review campaigns for SOC 2, ISO 27001, and PCI DSS.
- 95% reduction in IT effort required to process access request tickets.
- One place to view and audit access continuously and enforce least privilege access controls.
💡Recommended Watch →
Get the Job Done with ConductorOne
- View and manage identity across your environment. ** ** Pull fine-grained identity data from cloud and on-prem apps, directories, and infrastructure into one pane of glass for comprehensive visibility and control. Use powerful search and visualization tools to surface access insights and risks quickly.
- Streamline access certifications and auditor-ready reporting. Customize and run automated user access reviews with multi-step reviewer policies, Slack notifications, auto approvals, and zero-touch deprovisioning. Generate accurate, auditor-ready reports in one click.
- Enable self-service requests and enforce just-in-time access. Allow users to request access to any app, group, role, or permission with a self-service experience in Slack, CLI, or web app and automatic provisioning on approval. Move to zero standing privileges with automated JIT provisioning.
- Manage the entire identity lifecycle. Simplify onboarding and offboarding with automated multi-step provisioning and deprovisioning workflows, including delegated requests. Easily detect and revoke unused access, orphaned accounts, and deactivated users.
- Configure policy-driven access controls. Create zero-touch, conditional, and multi-step approval policies. Remove access based on time, non-usage, or changed justification. Force a re-request for especially risky access.
- Leverage AI for helpdesk automation. Automate helpdesk ticket processing with AI. Access Copilot reads, approves, and provisions helpdesk access requests. Your IT team will never touch another access request ticket.
Enjoy a developer-friendly experience. Technical teams love ConductorOne. Configure the platform using Terraform, request access with our command line (Cone), and leverage the ConductorOne API to drive automation.
ACCESS CONTROLS FOR THE MODERN ENTERPRISE
Secure your company with unified access visibility, just-in-time access, self-service requests, and automated access reviews—all from a single platform.




