Managing entitlements
What are entitlements?
Entitlements are access rights, permissions, or privileges to resources in an application.
For example, entitlements might be:
- Membership to a group
- Read access to a data table
- Assignment of a role
Entitlements allow ConductorOne to provide fine grained visibility into access rights and privileges for users and accounts.
When application data is ingested into ConductorOne via connector, file, or other data feed, ConductorOne identifies and creates resources and entitlements for those resources in the application. These resources are the basis of permission management.
To navigate to the entitlements in an application:
- Navigate to the application
- Click the Entitlements tab
Creating entitlements
Entitlements will be created automatically from connectors and data feeds into the application. Connectors do the heavy lifting of identifying essential resources (roles, groups, etc) inside of the application and sync’ing those and the corresponding entitlements to ConductorOne.
In the case where entitlements need to be manually created for a resource, this can be accomplished through entitlement creation or via API. To create a virtual entitlement:
- Click Create virtual entitlement
- Select the Resource type and set the name and description data
- Click Create
Managing entitlements
You may wish to manage different data elements on an entitlement. Start by navigating to the entitlement:
- Navigate to the application
- Click the Entitlements tab
- Click on the entitlement
From the entitlement detail page, you can:
Rename the entitlement
In ConductorOne we call attention to entitlements by showing them next to the resource. This is known as the entitlement slug. The slug is a short term that describes the access right or permission. The word or words inside that oval tell you exactly what permission the entitlement grants.
Entitlement slugs show up on individual entitlement summaries:
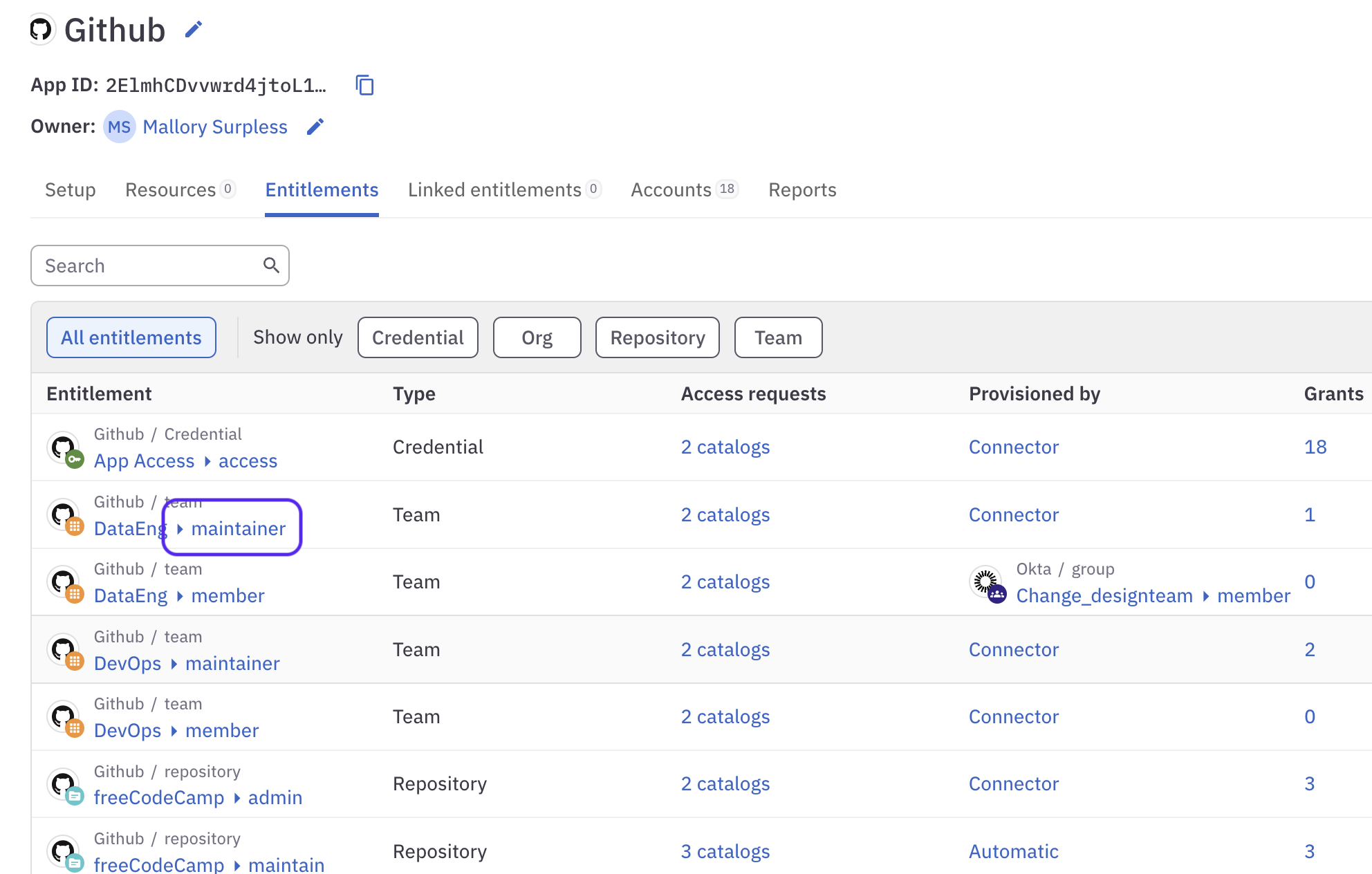
And are used to show all the entitlements on a particular resource:
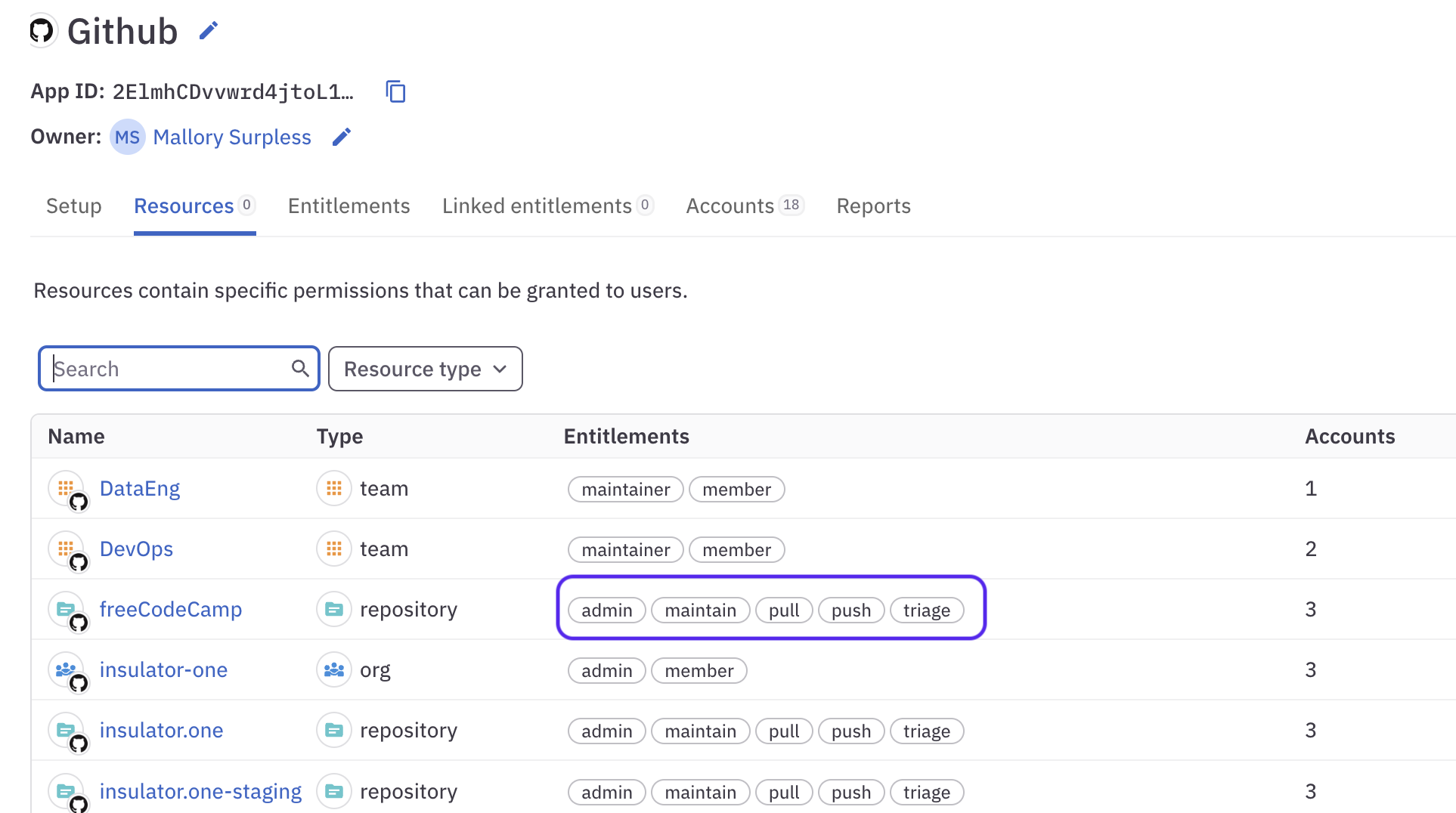
To edit the entitlement slug:
- Click Edit
- Set the entitlement Slug
- Click Save
Entitlement slugs are set automatically by connectors, but you can edit most of them. The exception is the credential resource, which has a single Access entitlement that cannot be renamed.
Setting access controls
Access controls define how an entitlement is granted, who can request it (and for how long), and what policies are used for reviewing, requesting, and revoking access.
- Click Edit on the corresponding access control box
- Enter the updated access control settings
- Click Save
Setting entitlement owner
Entitlement owners can be the target of policy approval steps. For example, you may require a entitlement owner to approve an access request for sensitive data or roles. To edit the resource owner:
- Click Edit
- Update the Owner field
- Click Save
View and manage grants
Grants are a list of who currently is granted an entitlement on a resource. To see the grants for the entitlement, click Grants.
Grants can be managed directly from this page. You can revoke a specific grant by clicking Revoke.
You can also change, extend, or even remove a grant’s expiration date on this page. Select a grant or multiple grants by clicking the checkbox on the left, then select Set expiration or Remove expiration from the bulk actions menu.
Setting entitlement attributes
You can create custom risk levels and compliance framework tags, and apply these tags to entitlements. You can then sort and select entitlements for access reviews and access profiles by compliance framework or risk level.
To create attributes:
- Navigate to Admin > Settings
- Click Edit on the Attribute values section of the page.
- In either the Compliance framework or Risk level field, type the name of the value you wish to add and press Enter.
- Repeat the process, adding additional attribute values as needed. Click the x next to any value to remove it from the list.
- When you’re finished, click Save and confirm your action.
If you remove an attribute that is currently in use in ConductorOne, that attribute will not be removed from any entitlements it is assigned to.
On the entitlement:
- Click Edit in the attributes box
- Select the correct risk level for the entitlement, or select None.
- If applicable, select any compliance frameworks that apply to the entitlement.
- Click Save.
You can now filter entitlements by attribute when creating an access review campaign or access profile.
Setting the alias
Aliases are useful short cut that can added to entitlements. Aliases can be used, for example, in the ConductorOne CLI tool to request access.
For example, in the command cone get aws-prod, aws-prod is the alias mapped to a production AWS role.
Deleting entitlements
To delete an entitlement:
- Click … in the top right corner
- Click Delete
- Confirm entitlement deletion
Entitlements (and resources) synced from a connector cannot be deleted. These entitlements represent the “truth” of the application that is connected. To delete these entitlements, they must be deleted in the connected app.
What is the “Access” entitlement
Every managed application in ConductorOne comes with a single resource and entitlement: the Credential resource and the Access entitlement on that resource. The access entitlement can be used to reference any Accounts that are in the application. This allows ConductorOne to treat accounts and access like resources and entitlements.
For example:
- If you want to make new accounts requestable in ConductorOne, set the corresponding access controls on the Access entitlement.
- If you want to run an access review on anyone who has any account in an application, select the Credential for the application.