Set up an Amazon Web Services (AWS) v2 connector
This is an updated and improved version of the AWS connector! If you’re setting up AWS with ConductorOne for the first time, you’re in the right place.
Capabilities
| Resource | Sync | Provision |
|---|---|---|
| IAM and Identity Center user accounts | ✅ | |
| IAM roles | ✅ | |
| IAM groups | ✅ | ✅ |
| Identity Center groups | ✅ | ✅ |
| Accounts via Permission Sets | ✅ | ✅ |
Known limitations
- Cross-account Assume Role is not currently supported
Gather AWS credentials
Configuring the connector requires you to pass in credentials generated in AWS. Gather these credentials before you move on.
A user with the Connector Administrator or Super Administrator role in ConductorOne and the ability to create an IAM Role in AWS must perform this task.
ConductorOne uses an IAM Trust relationship between your AWS Account and ConductorOne’s Service AWS Account. This is the AWS recommended method of sharing access to AWS Accounts. ConductorOne has a specially created and isolated AWS Account dedicated to the AWS integration. For advanced configurations, the only trusted entity should be the following ARN:
arn:aws:iam::765656841499:role/ConductorOneService
Get ConductorOne-provided External ID for AWS IAM Role
In ConductorOne, navigate to Admin > Connectors and click Add connector.
Search for AWS v2 and click Add.
Choose how to set up the new AWS connector:
Add the connector to a currently unmanaged app (select from the list of apps that were discovered in your identity, SSO, or federation provider that aren’t yet managed with ConductorOne)
Add the connector to a managed app (select from the list of existing managed apps)
Create a new managed app
Set the owner for this connector. You can manage the connector yourself, or choose someone else from the list of ConductorOne users. Setting multiple owners is allowed.
If you choose someone else, ConductorOne will notify the new connector owner by email that their help is needed to complete the setup process.
Click Next.
Find the Settings area of the page and click Edit.
Copy and save the External ID populated in the External ID field.
Create an AWS IAM Role for ConductorOne to use
In a new browser tab, sign in to your AWS Account using your existing credentials or SSO.
To support use of AWS Organizations: You must create this IAM Role in the management (formerly called master) account of the AWS Organization.
Navigate to the IAM Dashboard and select Roles > Create Role.
Select Custom Trust Policy and paste the following into the Trust Policy JSON editor, replacing
EXTERNAL_ID_FROM_C1_INTEGRATIONS_PAGEwith the External ID from ConductorOne.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::765656841499:role/ConductorOneService" }, "Action": "sts:AssumeRole", "Condition": { "StringEquals": { "sts:ExternalId": "EXTERNAL_ID_FROM_C1_INTEGRATIONS_PAGE" } } } ] }Click Next.
Skip Add permissions and click Next.
Give the role a name, such as ConductorOneIntegration.

Add any tags relevant to your organization and click Create Role.
Find the newly created role, and click on it to view the role details page.

Under Permissions Policies, click Add Permissions and select Create Inline Policy.
Switch to the JSON Editor tab and paste the following policy into the editor:
{ "Statement": [ { "Action": [ "iam:GetGroup", "iam:ListAccountAliases", "iam:ListGroups", "iam:ListRoles", "iam:ListUsers", "identitystore:GetGroupMembershipId", "identitystore:ListGroupMemberships", "identitystore:ListGroups", "identitystore:ListUsers", "organizations:ListAccounts", "sso:DescribePermissionSet", "sso:ListAccountAssignments", "sso:ListInstances", "sso:ListPermissionSets", "sso:ListPermissionSetsProvisionedToAccount" ], "Effect": "Allow", "Resource": "*", "Sid": "ConductorOneReadAccess" }, { "Action": [ "iam:AddUserToGroup", "iam:RemoveUserFromGroup", "sso:CreateAccountAssignment", "sso:DeleteAccountAssignment", "identitystore:CreateGroupMembership", "identitystore:DeleteGroupMembership", "sso:DescribeAccountAssignmentCreationStatus", "sso:DescribeAccountAssignmentDeletionStatus" ], "Effect": "Allow", "Resource": "*", "Sid": "ConductorOneProvisionAccess" }, { "Sid": "AccessToSSOProvisionedRoles", "Effect": "Allow", "Action": [ "iam:AttachRolePolicy", "iam:CreateRole", "iam:DeleteRole", "iam:DeleteRolePolicy", "iam:DetachRolePolicy", "iam:GetRole", "iam:ListAttachedRolePolicies", "iam:ListRolePolicies", "iam:PutRolePolicy", "iam:UpdateRole", "iam:UpdateRoleDescription" ], "Resource": "arn:aws:iam::*:role/aws-reserved/sso.amazonaws.com/*" }, { "Sid": "IAMListPermissions", "Effect": "Allow", "Action": [ "iam:ListRoles", "iam:ListPolicies" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "iam:GetSAMLProvider" ], "Resource": "arn:aws:iam::*:saml-provider/AWSSSO_*_DO_NOT_DELETE" } ], "Version": "2012-10-17" }A note about permissions. The permissions listed in the
"Sid": "IAMListPermissions"and"Sid": "AccessToSSOProvisiondRoles"sections are required only if you want to use ConductorOne to create assignments in the AWS Organization’s management account. In certain cases, you may also need to addiam:UpdateSAMLProviderto these sections.Click Review Policy.
Give the policy a name, such as ConductorOnePermissions and click Create Policy.
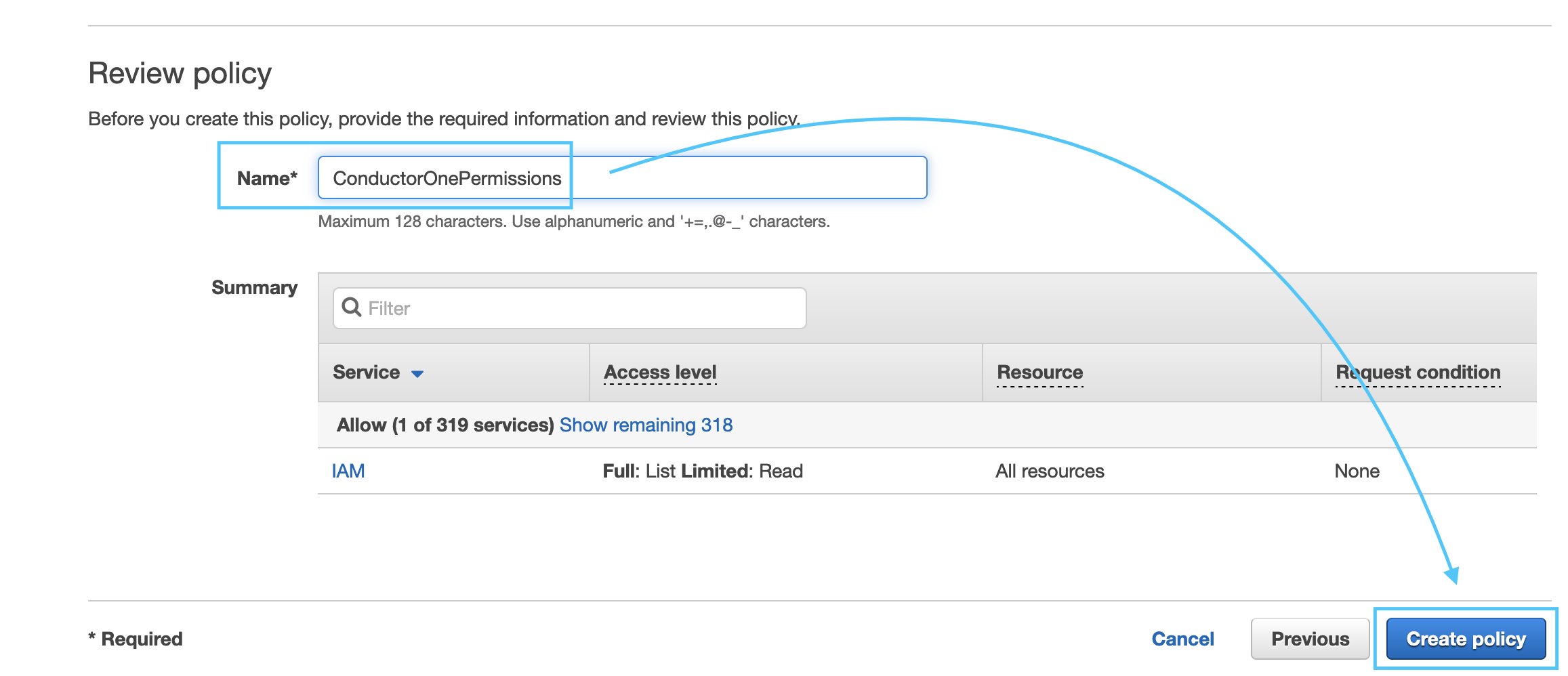
- Copy the Role ARN for the Role we created, it should look like:
arn:aws:iam::NNNNNNNNNN:role/ConductorOneIntegration.
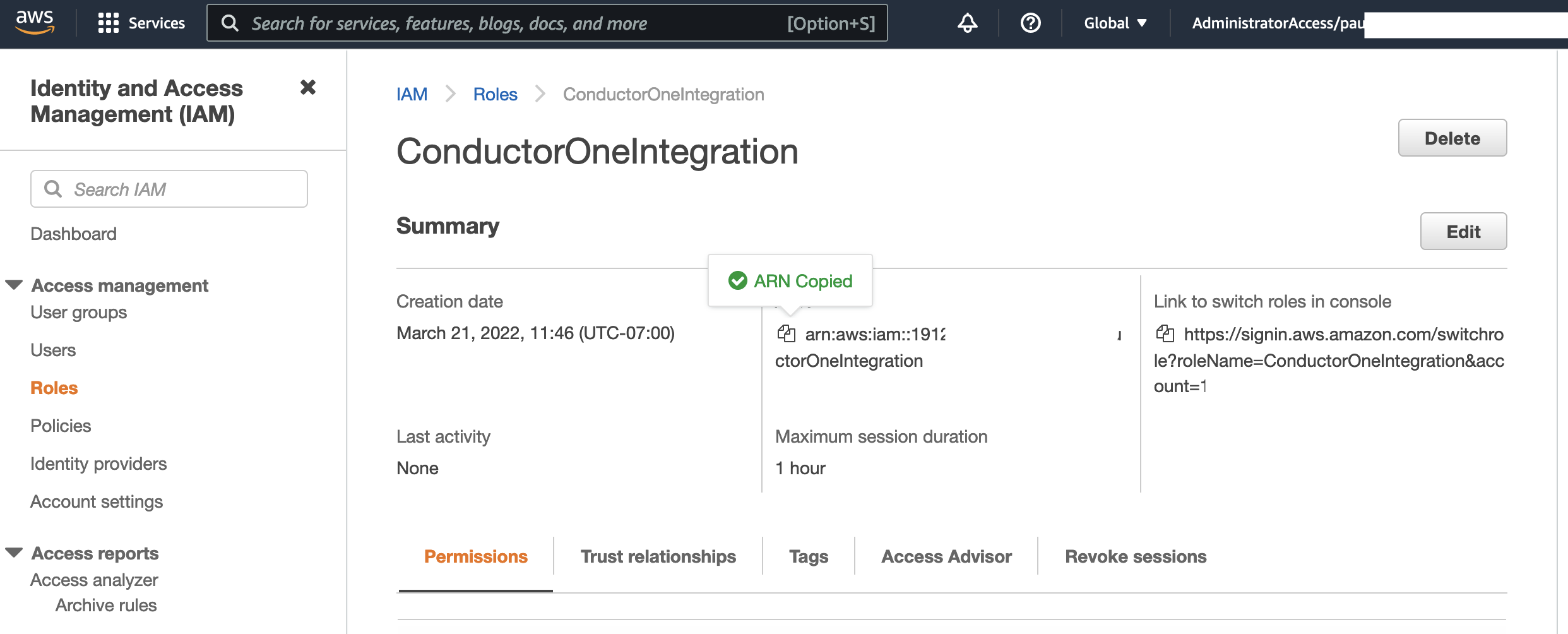
That’s it! Next, move on to the connector configuration instructions.
Configure the AWS connector
To complete this task, you’ll need:
- The Connector Administrator or Super Administrator role in ConductorOne
- Access to the set of AWS credentials generated by following the instructions above
Follow these instructions to use a built-in, no-code connector hosted by ConductorOne.
Return to the AWS v2 connector setup page in ConductorOne.
Find the Settings area of the page and click Edit.
Paste the AWS Role ARN into the Role ARN field.
Optional. Click the checkbox to Enable support for AWS Organizations.
If support for AWS Organizations is enabled, the IAM Role (as described in Step 2) must be created in the management (formerly called master) account of the AWS Organization. If the IAM Role is created on a member account and support for AWS Organizations is enabled, the integration will return a 400 error.
Optional. Click the checkbox to Enable support for AWS IAM Identity Center and select the region for AWS IAM Identity Center from the dropdown.
Optional. To enable ConductorOne to sync the statuses of SSO accounts, click the checkbox to Enable usage of the AWS IAM Identity Center SCIM API and enter the SCIM endpoint and access token in the relevant fields.
Click Save.
The connector’s label changes to Syncing, followed by Connected. You can view the logs to ensure that information is syncing.
That’s it! Your AWS connector is now pulling access data into ConductorOne.
Follow these instructions to use the Amazon Web Services connector, hosted and run in your own environment.
When running in service mode on Kubernetes, a self-hosted connector maintains an ongoing connection with ConductorOne, automatically syncing and uploading data at regular intervals. This data is immediately available in the ConductorOne UI for access reviews and access requests.
Step 1: Set up a new AWS connector
In ConductorOne, navigate to Connectors > Add connector.
Search for Baton and click Add.
Choose how to set up the new AWS connector:
Add the connector to a currently unmanaged app (select from the list of apps that were discovered in your identity, SSO, or federation provider that aren’t yet managed with ConductorOne)
Add the connector to a managed app (select from the list of existing managed apps)
Create a new managed app
Set the owner for this connector. You can manage the connector yourself, or choose someone else from the list of ConductorOne users. Setting multiple owners is allowed.
If you choose someone else, ConductorOne will notify the new connector owner by email that their help is needed to complete the setup process.
Click Next.
In the Settings area of the page, click Edit.
Click Rotate to generate a new Client ID and Secret.
Carefully copy and save these credentials. We’ll use them in Step 2.
Step 2: Create Kubernetes configuration files
Create two Kubernetes manifest files for your AWS connector deployment:
Secrets configuration
# baton-aws-secrets.yaml
apiVersion: v1
kind: Secret
metadata:
name: baton-aws-secrets
type: Opaque
stringData:
# ConductorOne credentials
BATON_CLIENT_ID: <ConductorOne client ID>
BATON_CLIENT_SECRET: <ConductorOne client secret>
# AWS credentials
BATON_EXTERNAL_ID: <External ID for the AWS account, generated by ConductorOne>
BATON_ROLE_ARN: <AWS Role ARN>
# Optional: Include if you want ConductorOne to provision access using this connector
BATON_PROVISIONING: true
# Optional: Include if you want to enable support for AWS Organizations (see note below)
BATON_GLOBAL_AWS_ORGS_ENABLED: true
# Optional: Include if you want to enable support for AWS IAM Identity Center
BATON_GLOBAL_AWS_SSO_ENABLED: true
BATON_GLOBAL_AWS_SSO_REGION: <Region for SSO identities (default is "us-east-1")>
# Optional: Include to enable ConductorOne to sync the statuses of SSO accounts
BATON_SCIM_ENABLED: true
BATON_SCIM_ENDPOINT: <SCIM endpoint>
BATON_SCIM_TOKEN: <SCIM access token>
If support for AWS Organizations is enabled, the IAM Role must be created in the management (formerly called master) account of the AWS Organization. If the IAM Role is created on a member account and support for AWS Organizations is enabled, the integration will return a 400 error.
See the connector’s README or run --help to see all available configuration flags and environment variables.
Deployment configuration
# baton-aws.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: baton-aws
labels:
app: baton-aws
spec:
selector:
matchLabels:
app: baton-aws
template:
metadata:
labels:
app: baton-aws
baton: true
baton-app: aws
spec:
containers:
- name: baton-aws
image: ghcr.io/conductorone/baton-aws:latest
imagePullPolicy: IfNotPresent
envFrom:
- secretRef:
name: baton-aws-secrets
Step 3: Deploy the connector
Create a namespace in which to run ConductorOne connectors (if desired), then apply the secret config and deployment config files.
Check that the connector data uploaded correctly. In ConductorOne, click Applications. On the Managed apps tab, locate and click the name of the application you added the AWS connector to. AWS data should be found on the Entitlements and Accounts tabs.
That’s it! Your AWS connector is now pulling access data into ConductorOne.
Configure the AWS connector using Terraform
Use the following Terraform script to integrate your AWS instance with ConductorOne.
Step 1: Get ConductorOne-provided External ID for AWS IAM Role
Log into ConductorOne.
Click Connectors > AWS Connector.
Copy and save the External ID populated in the External ID field. We’ll use this in Step 2.
Step 2: Use a Terraform script to set up the AWS integration
variable "EXTERNAL_ID_FROM_C1_INTEGRATIONS_PAGE" {
description = "ConductorOne-provided External ID for AWS IAM Role from Step 1"
type = string
}
resource "aws_iam_role" "ConductorOneIntegration" {
name = "ConductorOneIntegration"
assume_role_policy = jsonencode(
{
"Version" : "2012-10-17",
"Statement" : [
{
"Effect" : "Allow",
"Principal" : {
"AWS" : "arn:aws:iam::765656841499:role/ConductorOneService"
},
"Action" : "sts:AssumeRole",
"Condition" : {
"StringEquals" : {
"sts:ExternalId" : var.EXTERNAL_ID_FROM_C1_INTEGRATIONS_PAGE
}
}
}
]
})
inline_policy {
name = "ConductorOnePermissions"
policy = jsonencode({
"Statement" : [
{
"Action" : [
"iam:GetGroup",
"iam:ListAccountAliases",
"iam:ListGroups",
"iam:ListRoles",
"iam:ListUsers",
"identitystore:ListGroupMemberships",
"identitystore:GetGroupMembershipId",
"identitystore:ListGroups",
"identitystore:ListUsers",
"organizations:ListAccounts",
"sso:DescribePermissionSet",
"sso:ListAccountAssignments",
"sso:ListInstances",
"sso:ListPermissionSets",
"sso:ListPermissionSetsProvisionedToAccount"
],
"Effect" : "Allow",
"Resource" : "*",
"Sid" : "ConductorOneReadAccess"
},
{
"Action" : [
"iam:AddUserToGroup",
"iam:RemoveUserFromGroup",
"sso:CreateAccountAssignment",
"sso:DeleteAccountAssignment",
"identitystore:CreateGroupMembership",
"identitystore:DeleteGroupMembership",
"sso:DescribeAccountAssignmentCreationStatus",
"sso:DescribeAccountAssignmentDeletionStatus"
],
"Effect" : "Allow",
"Resource" : "*",
"Sid" : "ConductorOneProvisionAccess"
},
{
"Sid" : "AccessToSSOProvisionedRoles",
"Effect" : "Allow",
"Action" : [
"iam:AttachRolePolicy",
"iam:CreateRole",
"iam:DeleteRole",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:GetRole",
"iam:ListAttachedRolePolicies",
"iam:ListRolePolicies",
"iam:PutRolePolicy",
"iam:UpdateRole",
"iam:UpdateRoleDescription"
],
"Resource" : "arn:aws:iam::*:role/aws-reserved/sso.amazonaws.com/*"
},
{
"Sid" : "IAMListPermissions",
"Effect" : "Allow",
"Action" : [
"iam:ListRoles",
"iam:ListPolicies"
],
"Resource" : "*"
},
{
"Effect" : "Allow",
"Action" : [
"iam:GetSAMLProvider"
],
"Resource" : "arn:aws:iam::*:saml-provider/AWSSSO_*_DO_NOT_DELETE"
}
],
"Version" : "2012-10-17"
})
}
}