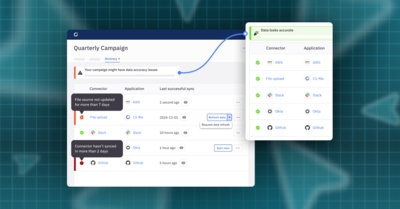

The NIS2 Directive: What to Know and What It Means for Identity Security
·Greg Howard & Brittany SmailAs of October 2024, all EU member states are required to have laws enforcing the NIS2 Directive, a cybersecurity framework aimed at protecting Europe’s critical infrastructure and services from cyberattack. Learn about NIS2, whether your business needs to comply, and best practices for meeting NIS2’s core identity security requirements.
Designing a Great User Experience
·Brittany SmailAs we continue to add new features and deeper capabilities to ConductorOne, our product designers and software engineers have the challenging task of making the platform even simpler and more intuitive to use. Learn all about their approach to UI design and check out our latest UI updates!
Closing the Door on Group Sprawl: Lessons from Spotnana's Security Journey
·Greg HowardGroup sprawl is real—and a major security concern for today's companies. In our latest webinar, Ben Godard, Head of Security at Spotnana, covered the risks created by groups and how to solve them. Here are the takeaways!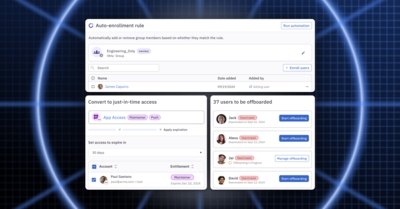

Growing Together: A Chat with the Summer Intern C1rew
·Brittany SmailOur engineering interns were integral to one of our biggest product updates this summer. Before moving on to the next steps in their degrees and careers, they chatted with us about working on the project and being part of the C1rew!
Identity Is the New Perimeter — Here’s How to Lock It Down
·Paul QuernaThanks to the success of zero trust, attackers are finding it harder to execute traditional breach tactics—so they've shifted their focus to identity. Here are practical steps you can take to shore up your defenses against identity-based attacks.
All Aboard: Analyzing Success in Cybersecurity with Ross Haleliuk
·Brittany SmailIn the newest episode of the All Aboard Podcast, ConductorOne CEO Alex Bovee is joined by Ross Haleliuk, author of Venture in Security and one of the most respected voices in the cybersecurity industry, to talk about what success in the industry means and where the industry is heading.
How Often Should You Run User Access Reviews?
·Brittany SmailRegularly reviewing who has access to your critical systems and data is an essential cybersecurity practice, but preparing and running user access reviews can be… daunting. How often should you run reviews to stay secure and compliant? And how can you make them less painful?
Stay in touch
The best way to keep up with identity security tips, guides, and industry best practices.