Unleash the power of autonomous identity governance
Automate security for all your human, non-human, and AI identities with one intelligent platform.
Trusted by It and Security @







The C1 platform
Identity is evolving fast. You don’t have time for siloed data and manual processes.
Centralize visibility and control with an AI-native solution that secures every identity, continuously and at scale.

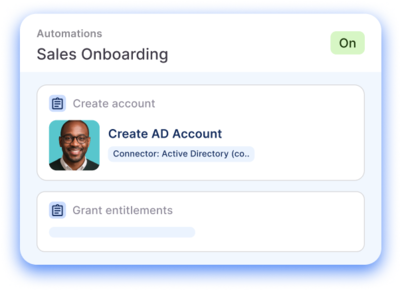
How conductorone works
Autonomous Identity Security Engine
Policies | Automations | C1 Agents
An intelligence layer that puts policy-driven workflows on autopilot
Unified Identity Graph
Your identity data lake
All your identity data— centralized, standardized, and queryable
C1 Connector Ecosystem
Cloud | On-prem | Custom
Fast, easy connection to every app

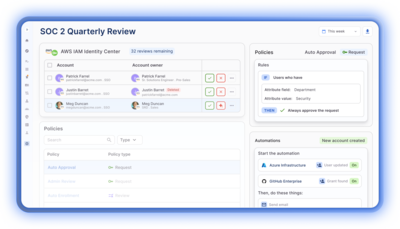
What you can achieve with C1
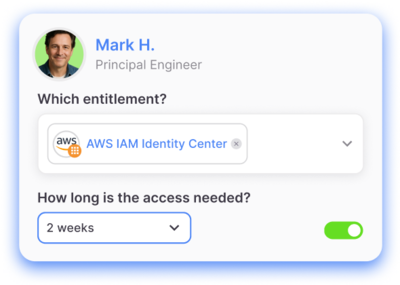
Frictionless least privilege
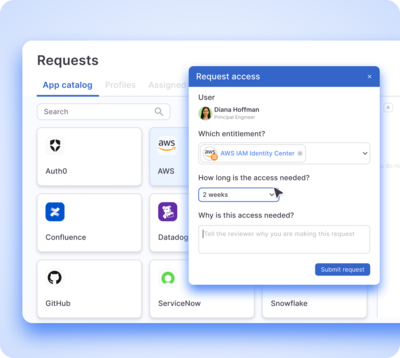
Less busywork, more business value
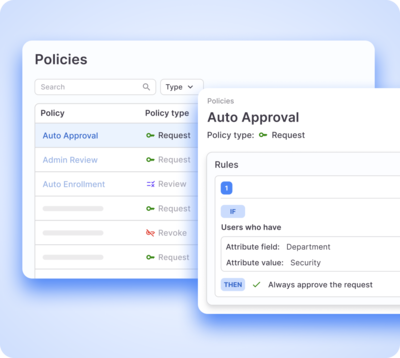
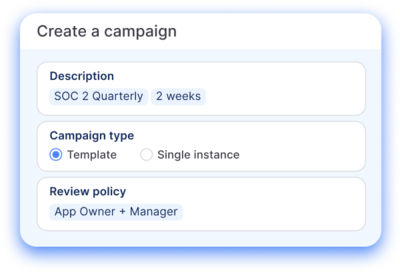
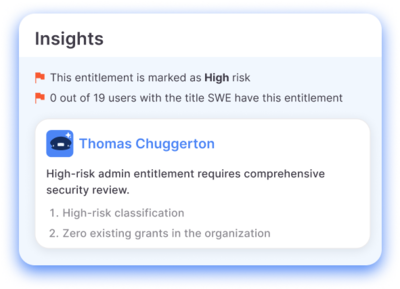
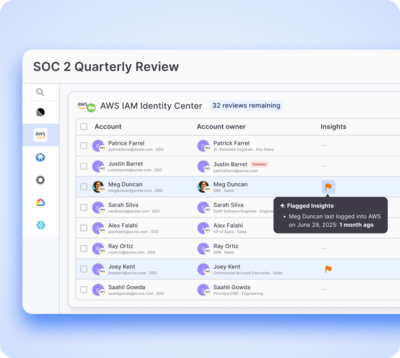
Always-on risk remediation
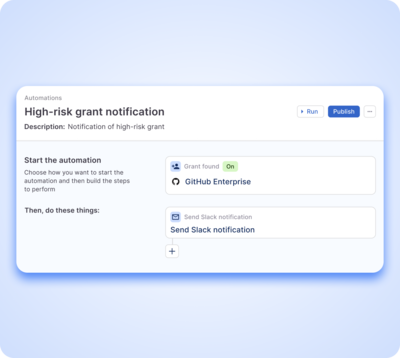
Continuous compliance
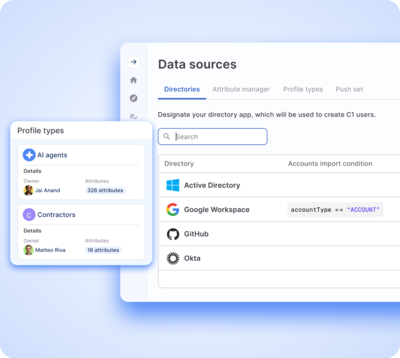
Unified identity data management
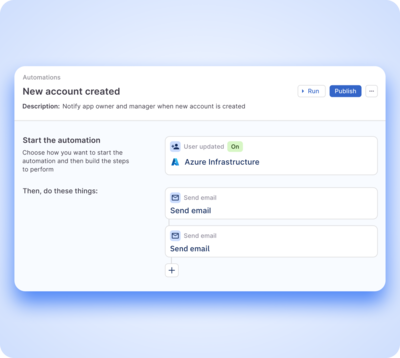
Your environment, your business, your platform
You shouldn’t lose months (or years) implementing an identity solution
C1 customers go live in an average of 4 weeks
Yeah, we’re impressed too
How? Connectors are a foundational component of our platform, not an afterthought. With 300+ out-of-the-box connectors and no-code custom connector options, all your apps—including legacy and homegrown—are integrated in just days or weeks.
Learn more about our connectors